By
N. C. B. Diop – Application Security Expert at Squad, DT Cybersecurity
Introduction
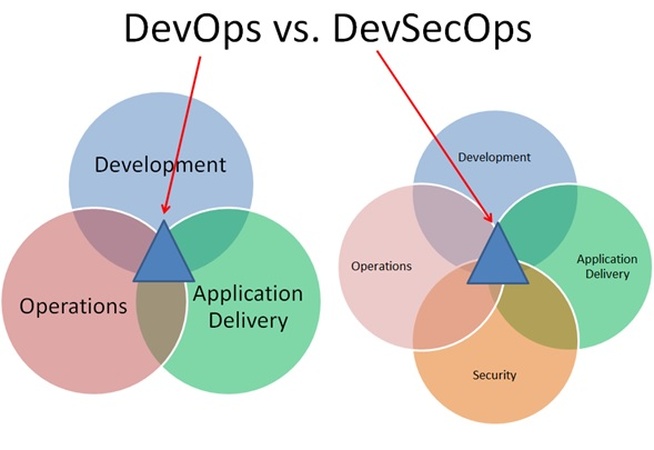
DevSecOps (Development-Security-Operations) is a bridge between development, test automation, and security. It involves every player in the software or application development cycle, making them responsible for security. In technical terms, its application requires the "Security by design" model. It encompasses a wide range of skills between technical architecture, security acceptance testing, and development.
Like DevOps, DevSecOps aims to implement the "Security by design" model while adopting the "awareness and training" aspect.
It seems very important to highlight the challenges and benefits, explain how such a model can be integrated, and present the vision that has been established along with the methodology and procedure to be implemented in order to achieve optimal results.
Note that for each environment, a model must be defined according to their ecosystem.
Challenges and benefits
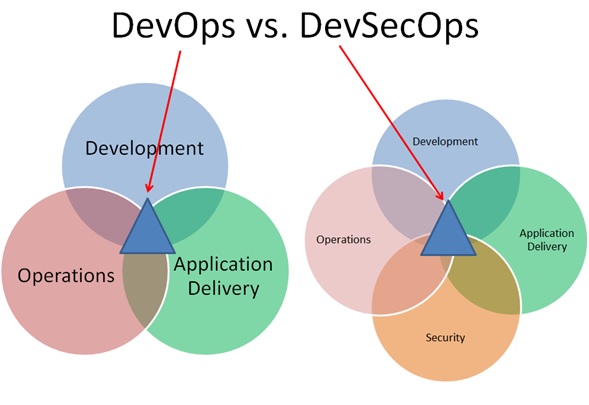
Many companies have not yet assessed the criticality of the lack of security in their applications. However, the challenges posed by a lack of security at the application level are critical. The financial impact is significant: it is estimated that it is 30 times cheaper to implement security upstream than during the production phase.
Raising awareness of these issues is important in order to alert companies seeking innovation to this model and encourage them to accept it.
For a company, the risks also concern its image or the theft of customer data. A company's reputation is very important in these times of attacks. With the increase in pirates and hackers in the digital world, prevention remains the best defense against cyberattacks.
When the application is checked for security during the design phase, it is 100 times cheaper to anticipate and correct vulnerabilities during the deployment phase.
The advantages of such an implementation are many and varied. There is consumer confidence, reputation, and brand awareness. Not to mention the reduction in maintenance costs associated with security patches saved for applications.
Agile security integration
Penetration testing
Penetration testing remains the most effective practice for minimizing risks associated with web or mobile applications that use web services. It is performed using commercial or free tools.
Code review
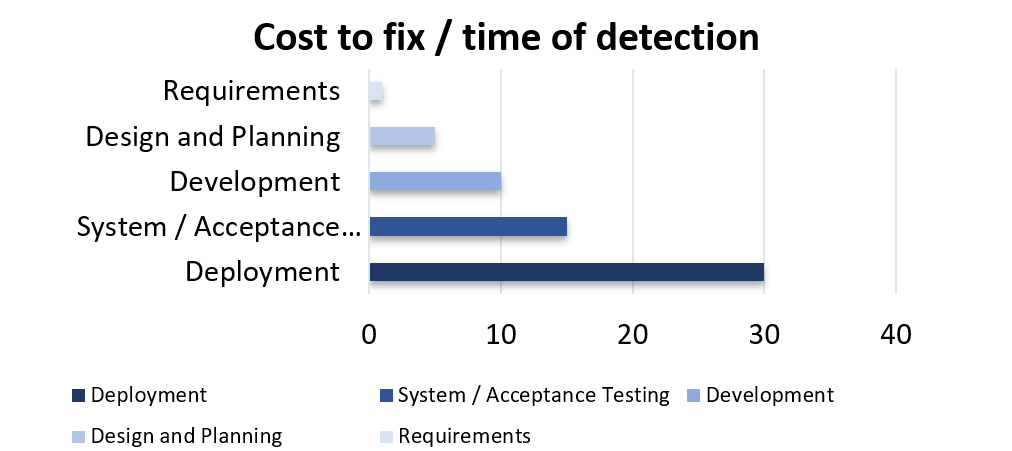
Static analysis tools enable the industrialization of vulnerability detection. Products such as Checkmarx provide an execution graph for detecting input data. The series of scans is performed during the development phase. For open source tools, the challenge remains the significant processing time and the number of false positives to be dealt with. HP Fortify is very effective in its ability to detect major problems, but Checkmarx remains the leader in code auditing solutions.
Vulnerability management
Libraries are often used, and patch management is not often performed. The Open Web Application Security Project (OWASP) offers a dependency-check plugin that checks whether a library is vulnerable.
Security test automation
It addresses four main challenges in the digital world, namely:
- Ensuring alignment with business requirements.
- Application assurance and confidence.
- Acceleration of production ramp-up.
- Ensuring the reliability of systems and their interoperability through a series of tests.
Product/Service Vision
Introduction to the secure SDLC model
The figure below shows the model that the overall SDLC must follow.

We distinguish five essential steps to be followed for each phase of the software development life cycle (SDLC).
Study phase:Security requirements are implemented to ensure that the defined specifications are met. A risk analysis must be carried out to identify needs and ensure that the design phase is conducted properly.
Design phase:An architectural framework must be implemented for guided model tracking.
Implementation phase:Code analysis is performed. This analysis is automated and programmed.
Acceptance phase:This phase determines whether the application is ready to move into the operational phase. It is reviewed by the security representative in the Digital Factory and the CISO and is based on
- Review of specifications, security procedures,
- The adequacy of the evidence provided in relation to the specifications,
- Formal approval from the security team.
- Maintenance phase
Maintenance phase:This includes the operational readiness maintenance (ORM) phase and the safety maintenance (SM) phase.
- As part of maintaining operational readiness, it is essential to incorporate a contingency and business continuity plan, define a backup plan, and implement patch management.
- In order to maintain security, it seems necessary to call on the IT security team. The latter is responsible for integrating the project in line with IT developments, managing vulnerabilities, and identifying and integrating the risks identified in the risk management matrix.
Procedure
It takes place in three major phases that ensure the adequacy of the results.
Implementation phase:This corresponds to the implementation of all environments. It includes the development environment. QA is responsible for managing this part in order to control the actions of developers.
Analysis phase:This corresponds to the scan launch phase. We distinguish between different types of scans depending on the maturity level of the application. The launch is automated.
Validation phase: This corresponds to the security validation phase. It must be carried out by the information systems security (ISS) team. Depending on the results obtained, a security acceptance test will be performed by the security analyst.
Conclusion
The automation of security testing is attracting more and more interest. Its advantage lies in its complexity, as it combines three different types of profiles into one: QA, developers, and security consultants.
At present, and based on our experience, it remains a major challenge to combine all these roles in a single person, a DevSecOps. It makes more sense to have a security test automation engineer with the right level of expertise in a development environment to ensure continuous compliance with security requirements in development projects.
Security is a very broad field, and DevSecOps is an ideology like DevOps that must be thoroughly understood before committing to it.