By Adrien C. - Cybersecurity Expert
Among the many areas of cybersecurity, steganography is often (unfairly) overshadowed by its illustrious cousin: cryptography.
That's why we're going to try to restore its reputation by explaining the basic principles and its usefulness in today's digital world.
Where cryptography (or the art of secrecy) consists of making a message unintelligible to anyone other than the recipient, steganography consists of concealing the original message within another message.
A metaphor often used to illustrate how they work is that encrypting a message is like putting your money in a safe with a lock and key, whereas concealing it would be like hiding the money directly by burying it in the garden.
It should be noted that it is entirely possible to use these two techniques simultaneously (and even highly recommended, depending on the issues at stake).
A thousand-year-old method
Like cryptography, steganography has been used in many ways throughout history, the most well-known example being invisible ink, which only becomes visible when exposed to heat. The arrival of microfilm later during World War II would change the game.
Here are a few examples from history:
- In China, messages were written on silk parchment, which was then covered with wax before being swallowed by the messenger (presumably to be recovered through "natural" means).
- In Persia, a message was tattooed on a slave's shaved head before sending him to the recipient once his hair had grown back: a relatively slow technique, but effective because it was possible to know whether the message had been read along the way.
- German spies used microdots to discreetly communicate secret information. These were photographs the size of a punctuation mark that could be cleverly hidden in legitimate text.
This example is illustrated in Edgar P. Jacobs' cult comic book series "Blake & Mortimer" in the album SOS Météore.

A digitalized method
With information technology now omnipresent in our lives and communications, steganography has naturally evolved toward more modern techniques. One of these, which is widely used, is called LSB (Least Significant Bit), which we will now discuss.
How can you hide information in an image?
Let's consider any image. It is actually a table of pixels. For each pixel, the color is encoded on 3 bytes as shown in the example below:
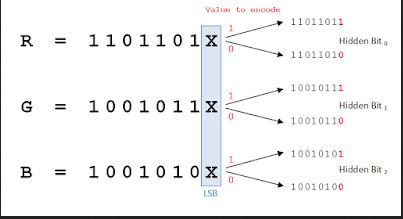
Each byte indicates the intensity of the corresponding color, on a scale ranging from 0 to 255. 255 corresponds to the native color. Slightly varying the value of the byte has only a minor graphical effect on the color.
Thus, if we change only the last bit of each primary color that makes up the color of each pixel (in other words, the last digit of each of the three numbers in the RGB code defining the color, also known as the "least significant bit") or even the last twobits, the change would be imperceptible to the naked eye: the difference would be only 3 out of a possible 255 shades, which is of course too subtle to be discerned by the human eye.
This is how messages are hidden in an image:
The message is converted into binary, then the last two bits of the red color of the first pixel are replaced by the first two bits of the information to be hidden.
Next, the last two bits of the byte that encodes the blue color are replaced by the next two bits of the text. This process is repeated for the green color and then with the next pixel.
At the end of the operation, it is virtually impossible to see any difference between the initial image and the image containing the information.

To hide an image within another image, the principle remains the same: instead of encoding the bits of text onto the least significant bits of the image that serves as the carrier, you simply encode the color bits of each pixel instead.
There are two methods:
➡ The first is simply to choose a carrier image that is much larger than the image to be hidden, because the goal is to separate a primary color from one pixel to another pixel and one-third of another (enough to insert 8 bits using the last two of each primary color).
➡ The second method involves using more bits for each color in each pixel. In this case, care must be taken not to take too much of the color, as the image once the other image has been steganographed may be visibly different from the original image.
We have just discussed one of thousands of steganography techniques: this one has the advantage of discreetly transmitting information (encrypted or not) because this information is contained within other conventional information (text, images, TCP frames, source codes, music tracks, etc.). Its main strength lies in two simple ideas: our senses (sight, hearing) are not capable of detecting tiny changes in an image or sound, and we do not know in advance that a file contains hidden information (although there are certain analysis techniques that can be used to detect it). Steganography, when combined with cryptography, can pose a threat, particularly in the context of illegal data exfiltration.


