Once again this year, we were present at the Toulouse Hacking Convention with a booth, a CTF team, and consultants invited to attend the conferences. This was the case for Mickaël, who shares his feedback on the presentations he particularly enjoyed:
Mask roms and masks of abstraction
To set the mood early in the morning, Travis Goodspeed, a reverse engineer from eastern Tennessee, explained his recipe for photographing microchips, extracting their physical bits, and converting them into bytes—all using various acids (hydrofluoric, nitric, peroxynitric, sulfuric), a microscope, and the appropriate software.
Obviously not to be replicated, this physical reverse engineering technique is perhaps the best way to understand new technologies at the lowest levels of abstraction...just like old video game cartridges.



Automating the extraction of secrets stored inside CI/CD
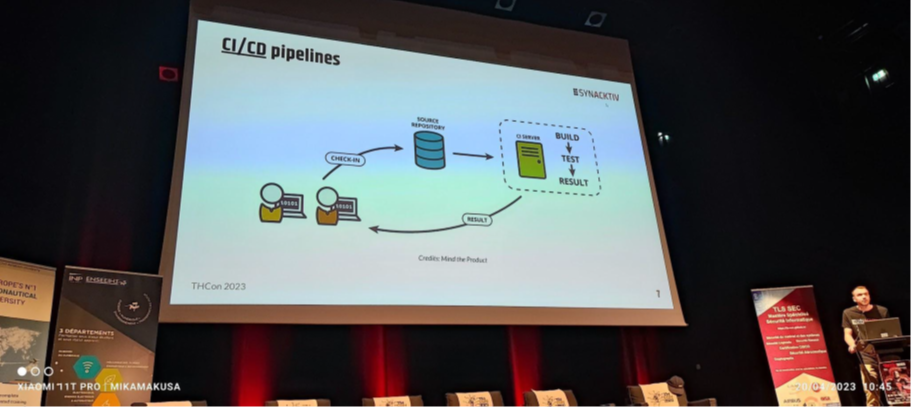
Théo Louis-Tisserand and Hugo Vincent emphasized the importance of properly securing sensitive information such as usernames and passwords when using CI/CD tools, demonstrating this with concrete examples. A fun approach that perfectly illustrates the risks.
The information in question passes through integration/deployment pipelines in an extremely insecure manner, making it very easy to extract. As such, they have also developed a tool to facilitate the extraction of this data.
At the same time, they emphasized the importance of using tokens to maximize the security of exchanges between applications and avoid injecting passwords into the application code.


Hash cracking: automation driven by laziness, 10 years later
Or how, using a tool he coded himself, David Soria showed us the different types of passwords, from the simplest to the most complex, whether predictable or not, easily crackable or requiring fairly advanced techniques or tools... He ended up coding his own tool that integrates and combines just about every password strategy in order to crack a large number of secrets on the fly. A pretty impressive demonstration!
Since then, he has been putting this tool and his skills at the service of companies wishing to identify vulnerabilities in their information systems.


Weaponizing ESP32 RF Stacks
When Romain Cayre and Damien Cauquil discoveredthe ESP32, a series of SoC microcontrollers with integrated Bluetooth and Wi-Fi management, they also wondered how far they could take it.
For example, spying on/sniffing Bluetooth communications, supporting protocols other than those originally intended by the hardware, turning it into a hacking tool... or lots of other "somewhat exotic" things.
After their intervention, the response seems to be positive: in the "right hands," this type of controller is capable of anything!

Hammerscope: Observing DRAM power consumption using Rowhammer
Straight from Intel's labs, Israeli duo Yaakov Cohen and Arie Haenel presented Hammerscope, a technique for measuring the energy consumption of RAM modules using Rowhammer.
As a reminder, Rowhammer is a hardware vulnerability affecting a large proportion of modern systems. At a high level, by performing certain memory access patterns, an attacker can insert bits without even writing them.
More information is available here: https://angelosk.github.io/Papers/2022/hammerscope.pdf
Why there is more to today’s attacks against online games than meets the eye
One of the least technical conferences of this edition, but nonetheless very interesting, with Marc Dacier reviewing the two main techniques used to cheat in online video games. He explained why they are relatively easy to implement and difficult to counter, both for players and for the operators of these same games...
Software-defined vehicle security: challenges, risks, and rewards
Drawing on his experience at Renault working on electric vehicle models, in which IT and the cloud have evolved to play an increasingly important role, Redouane Soum discusses the emergence of Software Defined Vehicles and how this development also brings with it potential cybersecurity risks related to increasingly connected vehicles and, consequently, the safety of their users.
Mickaël Dangleterre
DevOps Architect




