Risk management is now an integral part of information system security management (ISSM). Cyber risks have been a real challenge for several years now and can no longer be ignored, given the huge financial impact they can have on organizations. To this end, IT security teams, and in particular Chief Information Security Officers (CISOs), are pulling out all the stops to assess risks.
When it comes to risk management, there are several competing schools of thought. On the one hand, there is ISO 27005, an international standard that complies with the benchmark standard for risk management: ISO 31000[1]. It operates on the principle of continuous improvement, which is found in particular in ISO 27001 and developed around the famous Plan, Do, Check, Act ( PDCA)[2].
On the other hand, there is the Ebios Risk Management ( Ebios RM) method, created more than 25 years ago by the French National Cybersecurity Agency (ANSSI). This method, which is 100% Made in France, is very popular in France.[3], but struggles to find users abroad.
There is also the Harmonized Risk Analysis Method, abbreviated as MEHARI. This other standard was developed by the French Information Security Club (Clusif) for the first time in 1996.[4]. More recent than its two competitors mentioned above, this standard is aimed more at smaller organizations with a single site and a "centralized"information systems organization.
But then, what differentiates these risk management standards? Are they related? How can you know which of these three standards to apply within your organization?
ISO 27005, Ebios, MEHARI... What exactly are we talking about?
While certain similarities can be found between the three standards, their origins and contexts of creation are completely different.
ISO 27005 derives directly from ISO 27001. It operates according to the continuous improvement process and is presented as a sub-process of the latter.[6].
The main stages of ISO 27005 thus refer directly to the PDCA process of ISO 27001. Beyond the necessary consistency between the functioning of these two standards, the latter also enables continuous improvement in risk management within the organization concerned.
Risk analysis is one of the essential steps in implementing an information security management system (ISMS) within an organization. This aspect further reinforces the inherent complementarity between ISO 27001 and ISO 27005.
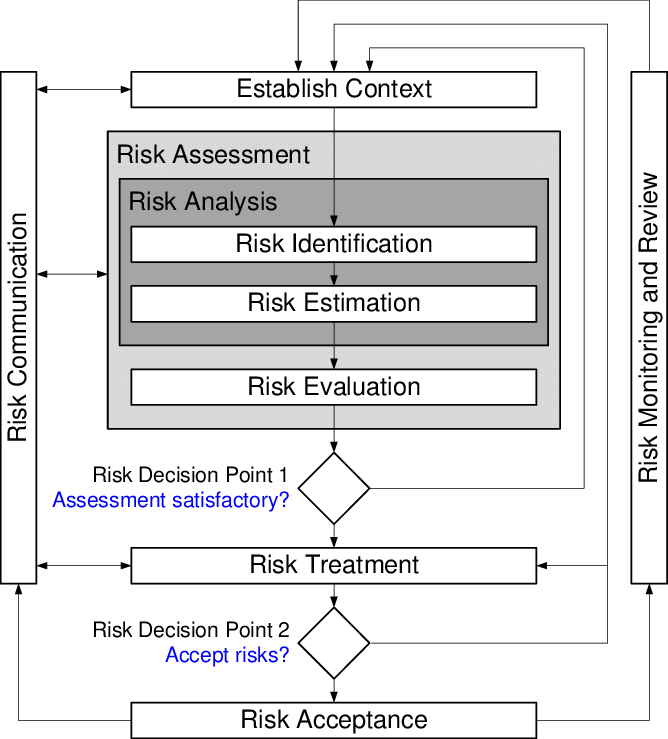
Diagram detailing the risk analysis process produced under the ISO 27005 standard
Source: https://www.researchgate.net/figure/ISO-IEC-27005-Risk-Management-Process-16_fig2_320821063
As forEbios RM, the context in which it was created is completely different. This method was developed in 1995[7] by ANSSI, with a twofold challenge at the time: on the one hand, it was created only five years after the official launch of the World Wide Web[8]. On the other hand, the aim was to offer a more iterative approach than ISO 27005 "without proposing a method in the strict sense," according to Club Ebios[9]. Today, this method is mainly applied in France[10].
Comprising five workshops, this method offers a progressive risk analysis, enabling an understanding of the organization's entire ecosystem. By identifying business values, followed by the drafting of strategic and then operational scenarios, and ending with the risk treatment phase, Ebios RM has the advantage of being applicable to the vast majority of organizations, while guaranteeing a comprehensive view of risks.
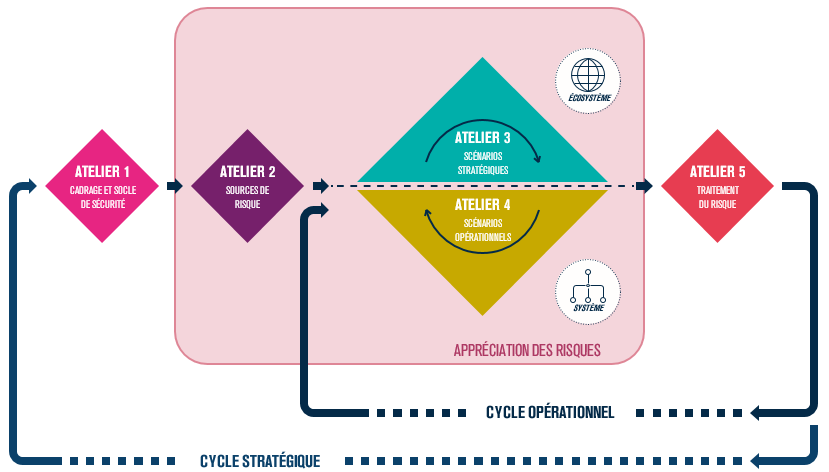
Presentation of the five iterative workshops of Ebios RM
Source: https://www.all4tec.com/blog/guides/ebios-risk-manager/
Another risk management standard also emerged in the second half of the 1990s: MEHARI. Like Ebios RM, it is an iterative risk management method consisting of four steps:
- Research and analysis of potential malfunctions
- Diagnosis of the state of security services
- Residual risk assessment
- Definition of security plans
Created by Clusif, this standard not only sets out risk identification and assessment procedures. It also aims to "highlight measures that can be taken to reduce risks to an acceptable level."
However, this standard also remains closely linked to ISO standards. According to Clusif itself, MEHARI is particularly suitedto "companies or organizations that want their security services to be fully aligned with the controls set out in ISO 27002: 2013[12]."
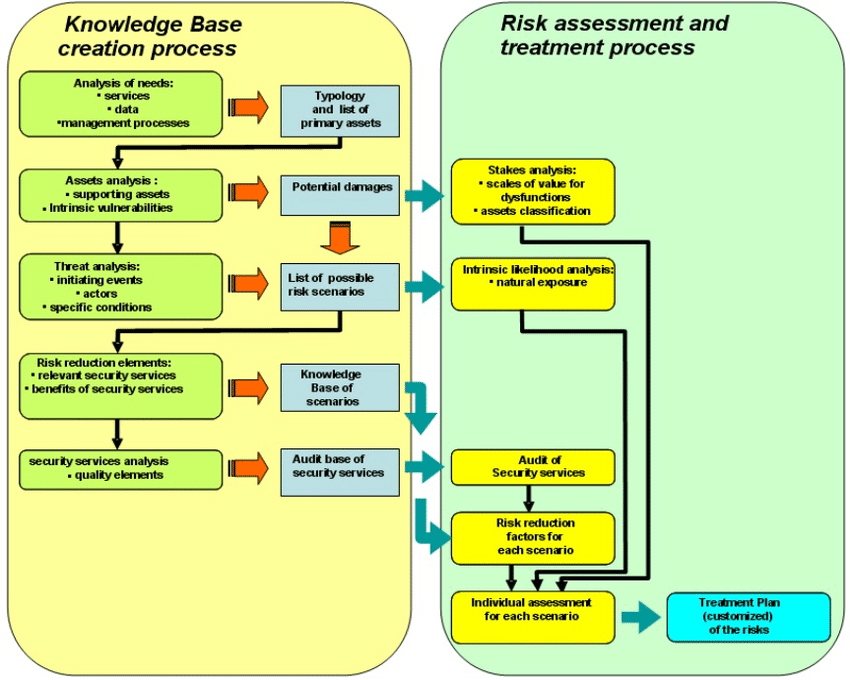
MEHARI approach
Source: https://www.researchgate.net/figure/The-MEHARI-Risk-Management-Process-Source-16_fig3_308887372
MEHARI
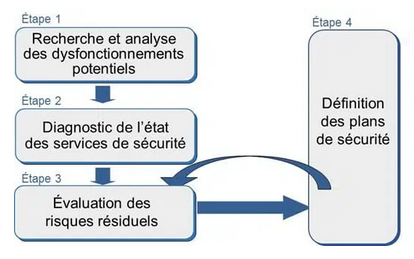
Diagram representing the iterative approach of MEHARI
Like its two other "competing" standards, MEHARI begins with an overall assessment of the organization's activities on which we wish to conduct our risk analysis. The main objective of this first phase is to detect potential malfunctions that could have more or less serious consequences for the organization's information system.
However, the second stage is very different from ISO 27005 orEbios RM, as it consists of an assessment of the state of the company's security measures. Through interviews with various security managers, both operational and organizational, it provides an overview of the general functioning of security measures within the IS.
Finally, closely linked, steps 3 and 4 of MEHARI mark the end of the process, first with the risk analysis itself, conducted differently from the other standards seen above. In addition, this analysis results primarily from the diagnosis of security measures considered "flawed" in step 2, and therefore from the treatment plans to be implemented in order to reduce these risks. This is the purpose of the fourth step, which consists of defining these security plans.
MEHARI differs from ISO 27005 andEbios RM in the way it analyzes risks and in its references. Whereas ISO 27005 is linked to ISO 27001, MEHARI is linked to ISO 27002. Nevertheless, its iterative approach, consisting of four stages, is reminiscent of the structure of Ebios RM.
Different operation and strengths
The fact that these three frameworks are distinct is primarily due to the fact that each one presents different approaches to risk management. This difference in understanding cyber risks explains, among other things, why organizations choose to recommend one of these frameworks in particular.
For example, ISO 27005 is almost always used by organizations that are already ISO 27001 certified. This choice is primarily made for consistency and continuity by CISOs, who legitimately prefer to remain within the ISO environment in order to optimize the security of their information systems. As we have seen, the cyber risk management process described in ISO 27005 fits perfectly into the Plan Do Check Act cycle of its big sister, ISO 27001. Furthermore, in the field of information security, the ISO 27000 standards are a benchmark, which explains why many CISOs and organizations decide to turn to them, particularly with regard to cyber risk management.
Ebios RM, meanwhile, offers a different approach to cyber risk management. Its presentation and iterative process allow participants, workshop after workshop, to become fully aware of the ecosystem in which their information systems operate. This awareness of the external and internal environment surrounding the organization's assets enables the CISO to easily identify the most significant risk scenarios. Once these scenarios have been identified and detailed—via strategic and operational scenarios—it becomes much easier to choose the measures to be implemented in order to reduce the risks identified beforehand.
MEHARI innovates in two important ways. First, like Ebios RM, it is an iterative method. Several workshops are planned to better understand the organization's environment. Second, MEHARI offers different knowledge bases depending on the size of the organization concerned by the risk analysis. The method therefore automatically adapts to the needs of the organization in terms of size and workforce. These knowledge bases are also linked to the ISO 27002 standard for the treatment of identified risks.
A difference in status between the three standards
Although Ebios RM is a recognized method in France, it has struggled to achieve similar success abroad. As a reminder, the ISO 27005 standard is directly dependent on the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It is therefore developed by two independent private organizations.
Conversely, Ebios RM was created by ANSSI, the French government agency responsible for information system (IS) security. As a result, this standard is more naturally linked to the French business ecosystem, which explains both its successful deployment in France and its difficulties in being exported internationally.
MEHARI has yet another status, as this standard was developed by Clusif, an "association promoting cybersecurity, bringing together companies and government agencies to develop best practices for digital security."It is therefore neither a government agency nor a standards body such as ISO or IEC. Its scope of application and/or deployment differs from the other standards mentioned above.
But in the end, who wins?
The main idea behind this article and these comparisons is not to highlight one standard over another or to disparage them. Rather, the aim is to understand how they were developed and in what contexts. It is also relevant to note the similarities that may exist between them, in order to understand why certain organizations may prefer one standard over another.
Ultimately, the key is for each organization to find the standard that best suits its internal operating methods and its own objectives in terms of information system security. With new threats looming over businesses and the colossal impact they can have, particularly in financial terms, the most important thing is for top management to be aware of this hostile environment in order to protect its most valuable assets.
Whether it is ISO 27005,Ebios RM, or MEHARI, these three standards have been developed to respond as effectively as possible to the challenges posed by today's cyber threats.
More broadly, these three standards, although different, are based on the same logic that can be found in each of them, namely a first part devoted to establishing a context within the organization, followed by a second step to identify the risks associated with this context and develop risk scenarios, which are then assessed and classified in a third step. Finally, a fourth and final stage involves implementing a risk treatment plan to reduce those risks that are most likely and/or have the greatest impact on the organization.
Finally, it should also be borne in mind that these three standards are likely to evolve in the coming years in order to continually adapt to the needs of organizations in terms of cyber risk management. It would therefore be useful to repeat a comparison between these three standards in order to study the potential impact of these changes on how organizations adopt them.
[1] https://www.isit.fr/fr/article/quel-est-le-lien-entre-ebios-rm-la-norme-iso-27005.php
[2] https://www.c-risk.com/fr/blog/iso-27005
[3] https://www.isit.fr/fr/article/quel-est-le-lien-entre-ebios-rm-la-norme-iso-27005.php
[4] https://clusif.fr/services/management-des-risques/les-versions-de-mehari/mehari-standard/
[5] https://clusif.fr/services/management-des-risques/les-versions-de-mehari/mehari-standard/
[6] https://www.skills4all.com/cybersecurite-tout-ce-que-vous-devez-savoir-sur-la-norme-iso-27005-risk-manager/
[7] https://cyber.gouv.fr/la-methode-ebios-risk-manager
[8] https://www.bercynumerique.finances.gouv.fr/breve-histoire-du-web
[9] https://club-ebios.org/site/category/origine/
[10] https://www.isit.fr/fr/article/quel-est-le-lien-entre-ebios-rm-la-norme-iso-27005.php
[11] https://clusif.fr/services/management-des-risques/les-fondamentaux-de-mehari/
[12] https://clusif.fr/services/management-des-risques/les-versions-de-mehari/mehari-standard/
[13] https://clusif.fr/le-clusif/




