Before discussing Confidential Virtual Machines, let's talk about confidential computing. Confidential computing is an industry term defined by the Confidential Computing Consortium (CCC), which is part of the Linux Foundation. It is dedicated to defining and accelerating confidential computing.
The CCC defines confidential computing as follows:
" Data protection in use by performing calculations in a trusted execution environment (TEE) based on attested hardware." (TEE=Trusted Execution Environment)
These TEEs prevent unauthorized access or modification of applications and data during computation, ensuring that data is always protected. TEEs are a trusted environment that guarantees data integrity, confidentiality, and code integrity.
Any code outside the TEE cannot read or tamper with data inside the TEE. The confidential computing threat model aims to remove or reduce the ability of a cloud provider operator or other actors in the tenant domain to access code and data during execution.
Now, let's talk about Confidential Virtual Machines in Azure. The purpose of this article is to introduce you to this Azure service, which is designed for businesses with very high security demands and requirements.
Confidential virtual machines have been available in Azure for some time now, and Microsoft is constantly improving them.
What is an Azure confidential virtual machine?
A Confidential Virtual Machine is a virtual machine that uses hardware-based encryption technology to ensure a high level of confidentiality for data during execution. These confidential virtual machines enable sensitive workloads to be executed.
The benefits of using confidential virtual machines
- Hardware-Based Encryption (SGX):
Confidential Virtual Machines leverage Intel Software Guard Extensions (SGX) technology to provide a secure environment in which sensitive data can be processed confidentially. SGX allows memory areas to be isolated, creating "secure enclaves" where data can be processed without being exposed to other parts of the virtual machine or host system.
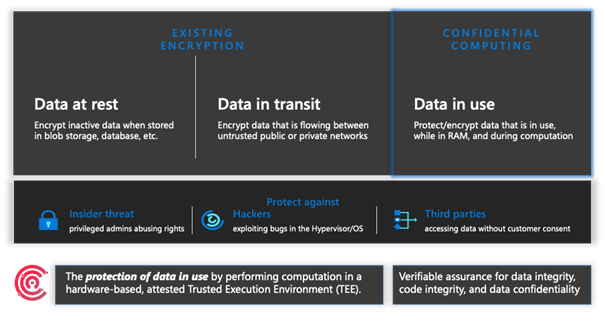
Example:
In this example:
- Thehost is the "untrusted" component. Your enclave application runs on the host. The host is an untrusted environment. When you deploy enclave code to the host, the host cannot access that code.
- Theenclave is an "approved" component. The application code, along with its cached data and memory, runs within the enclave. The enclave environment protects your secrets and sensitive data. Ensure that your secure computations occur within an enclave.
- Isolation of encryption keys:
The encryption keys used by Confidential Virtual Machines are stored and processed securely within SGX enclaves, preventing unauthorized access even by system administrators. This enhances the security of encryption and decryption operations.
- Protection against physical attacks:
Confidential Virtual Machines are designed to resist physical attacks such as direct access to physical memory. Data inside SGX enclaves remains protected even if the underlying machine is physically accessed.
And many more, such as:
- Customizable attestation strategies to ensure host compliance prior to deployment
- Cloud-based confidential operating system disk encryption before first boot
- Virtual machine encryption keys that the platform or client owns and manages
- Secure key release with encryption link between successful platform authentication and virtual machine encryption keys
- Dedicated virtual Trusted Platform Module (TPM) instance for attestation and protection of keys and secrets in the virtual machine
- Secure boot feature similar to Trusted Boot for Azure virtual machines
Limits
Virtual machines do not support network acceleration, which also excludes them from VNET encryption (acceleration is a prerequisite).
Some services are not supported: Backup and Site Recovery. A dedicated backup must therefore be provided.
Confidential virtual machines support the following virtual machine sizes:
- General use without local disk: DCasv5 series, DCesv5 series
- General use with local disk: DCadsv5 series, DCedsv5 series
- Optimized memory without local disk: ECasv5 series, ECesv5 series
- Optimized memory without local disk: ECadsv5 series, ECedsv5 series
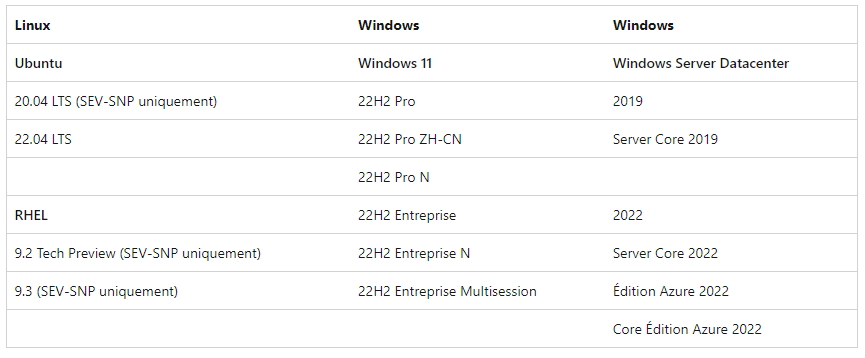
Confidential virtual machines support the following operating systems:
Conclusion
Azure Confidential Virtual Machines offer a robust solution for meeting confidentiality and data protection requirements in the cloud.
Using SGX technology, Azure enhances the security of sensitive workloads, opening up new possibilities for the secure execution of services and applications in the cloud.
This advance helps to strengthen the confidence of businesses and users in the use of cloud services, while offering a high level of confidentiality for their sensitive data.
By adopting Azure Confidential Virtual Machines, organizations can benefit from a more secure approach to processing sensitive information, helping to protect privacy and comply with data security regulations.
To go further... Azure confidential virtual machines vs. AWS Nitro Enclaves
These two cloud services are very similar, with Azure Confidential VM and AWS Nitro Enclaves both emphasizing security, but certification and compliance guarantees may vary. It is important to verify specific certifications to meet organizational requirements.
Azure VM Confidential integrates naturally into the Azure ecosystem, while Nitro Enclaves integrates with the AWS ecosystem. The choice between the two may depend on the set of tools and services already used by an organization.
In short, there is no major difference between these two solutions. It will essentially depend on your needs and what you already use in the cloud.
Nicolas VACCARO
Cloud Engineer









