EASM stands for External Attack Surface Management. This service simulates the position of an external attacker and all the public information they can gather to prepare an attack on your infrastructure. I helped a client (a mid-sized company starting to modernize its cybersecurity) implement this service. Here is my feedback:
Opportunity
The purpose of my assignment was not EASM, but while talking with the CISO, it became clear that the company, which owns several brands, had issues with listing and controlling its online exposure. I then told him about Defender EASM because they were in the process of migrating to Azure.
By explaining that the solution was free for 30 days and required few resources to implement, the POC was launched.
Implementation
After creating an EASM resource, which is extremely simple, you need to create a seed, and from there, EASM operates on its own.
This seed contains your domain names, host names, and public IP ranges. With this information, EASM will scan various sources of information (DNS server, public database) on a weekly basis.
The initial discovery takes 24 to 48 hours. After this period, we obtain the following result:
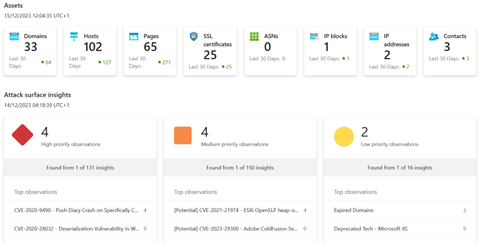
This provides us with information about:
- External domains
- Hosts
- Pages
- SSL certificate
- ASN (Autonomous System Number, used in BGP)
- IP block
- IP
- Contact
Most of the data comes from DNS servers. For example, "contact" lists the people who appear in a WhoIs search .
This ensures that only people who are still working for the organization remain.
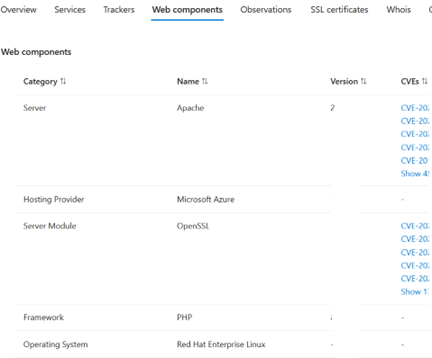
Example of information for one host: this tells us that certain software programs have CVEs.
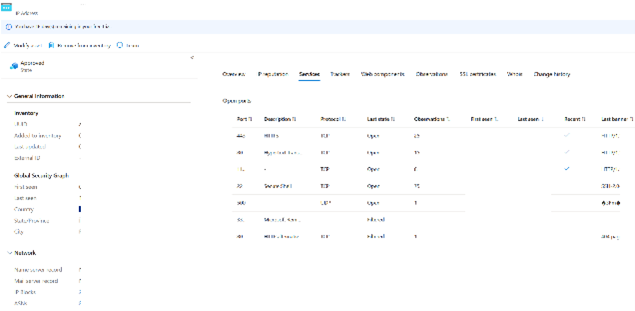
Example of information retrieved from one IP address with an open port scan:
Point of attention
The tool retrieves information based on your seed. If your organization has a common name, there may be numerous results. These must then be sorted. We are billed according to the number of items found: €0.011 per resource per day (€4 per year) as of December 15, 2023, which hinders the prioritization of vulnerabilities found.
After the first scan, you must then make a selection to ensure that you only have your organization's resources (you can also configure your seed to exclude unrelated IP ranges and domain names).
There does not appear to be any control over the seed that is used. An attacker could use this to accurately map a potential target (already possible with a number of other tools).
Benefits for the customer
- Replacement of the certificate management tool: EASM provides a list of external certificates with their expiration dates:
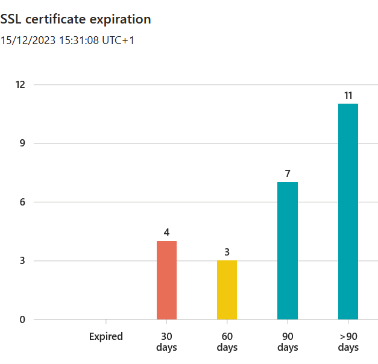
By connecting EASM to Log Analytics and Sentinel, alerts are generated and sent to the responsible teams. This eliminates the need for an internal management tool where recording is manual and frequently overlooked.
- Better visibility and control over your external footprint (forgotten domain names that are still being billed, etc.)
- Contextualization of alerts in relation to different reference systems:
- The GDPR section covers authentication methods, cookies with a lifetime of more than one year, and third-party cookies.
- OWASP Top 10 and CWE Top 25 classify vulnerabilities according to these standards.
- CISA (Cybersecurity and Infrastructure Security Agency) is the most interesting for prioritization because it indicates vulnerabilities that are actively being exploited.
It should be noted that although the interface is supplemented with a wealth of information on vulnerabilities and their associated remedies, someone with expertise in vulnerability management will be able to get the most out of the service.
Once the first scan has been performed and the most urgent fixes have been made, the product may seem unnecessary for an organization that does not have a large web presence. It was decided to start with a permanent seed in order to retrieve certificates (use case mentioned above) and, every six months, create a new EASM resource (to take advantage of 30 days free) and perform a full scan. The price for a large infrastructure can be significant; the items billed are hosts, domains, and IPs.
Rex for a large organization
Another client (a multinational company) had difficulty managing its URL repositories and the CSPs hosting them. The Defender solution proved its worth here too, with host classification by CSP. Shadow IT detection can also be included in the scope. It should be noted that the tool is able to identify hosts whose URL does not include the name of the organization by studying DNS records.
This provides a very good overview of existing (and sometimes forgotten) services.
My conclusion
If you are already an Azure customer, the solution stands out for its ease of implementation. Its day-to-day use requires personnel trained in vulnerability management to prioritize and handle reports effectively. It is also important to take the time to validate the inventory to avoid significant billing charges.
The option of 30 days free when creating a resource allows you to try it out and see if the solution is right for your organization.
There are other solutions for EASM (CrowdStrike's FalconSurface, Palo Alto's Cortex Xpanse, etc.). This feature is essential for CTI or vulnerability management teams and allows them to detect an entry point that an attacker will use!
Matthew GAILLARD-MIDOL
SecOps & CloudSec Practice Leader






