The dependence of our administrative, economic, political, and military activities on digital technology is no longer a matter of moral or philosophical debate, but a fact. Given this reality, their exposure to cyber threats has never been so worrying, and will only become more so in the future. A common-sense conclusion is therefore obvious: when cyber issues affect the integrity of a state or a group of states, the security of these information systems must no longer be solely in the hands of private companies, but must also be regulated by national or supranational entities through regulatory frameworks.
Although this is not intended to be an exhaustive list, it is essential to examine three of these emblematic regulatory frameworks: the Military Programming Law (LPM) in France, the European Union's Network and Information Security Directive (NIS-2), and the IT security standards established by the National Institute of Standards and Technology (NIST-CSF 2.0) in the United States. Analyzing these legislative frameworks will provide a comprehensive understanding of their implications, their specific features, their commonalities, and how they intersect, in order to understand how they shape the global cybersecurity landscape.
The Military Programming Act (LPM)
 Source: ANSSI
Source: ANSSI
History
The LPM is intended to be a political and defense strategy project in a context of rearmament and conflict on European territory. Voted on every five years, the most recent being in 2023, it would be apocryphal to say that this law only concerns companies in the military sector. It applies to all Operators of Vital Importance (OVIs), i.e., all private and public entities that are essential to the proper functioning of the nation. It therefore logically places particular emphasis on areas relating to information system security.
The LPM aims to ensure that France, and more specifically OIVs, strengthen the resilience and protection of their infrastructure and IT systems as much as possible.
Scope
Before delving deeper into the specifics of the law, it is first necessary to define its scope.
The LPM is a French law that applies only to OIVs.
The latter are defined in Article R. 1332-2 of the Defense Code as all activities contributing to the production and distribution of goods or services that are essential to health, sovereignty, economic functioning, and the maintenance of defense capabilities, or that represent a serious danger to the population. This also includes organizations that, as part of their activities, have the, management, or use of an establishment, structure, or facility whose damage, unavailability, or destruction, as a result of an act of malice, sabotage, or terrorism, would directly or indirectly seriously undermine the war or economic potential, survival, or survival capacity of France and its population.
Am I affected?
More specifically, twelve sectors of activity are included in this definition, namely:
- The civil, military, and judicial activities of the state
- Activities related to health, water management, food, energy, and finance
- Activities related to transportation, communications, industry, and research
If a company has a business located on French territory that corresponds to one of these sectors of activity, then that company may be considered an OIV, and its IT systems related to those activities may be considered Information Systems of Vital Importance ( SIIV). Each SIIV must then undergo LPM certification if it wishes to remain in operation.
Obligations
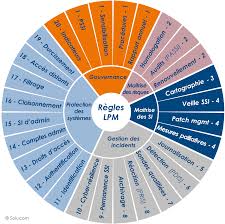
Through the LPM, France imposes guidelines on SIIVs divided into twenty categories, themselves divided into five higher-level areas, to ensure their security and resilience:
Governance rules
- Information Systems Security Policy (ISSP)
- Monitoring of indicators
Risk management rules
- Safety certification
Rules relating to IS control
- Mapping
- Policy on maintaining safety conditions
Incident management rules
- Log actions
- Enable log correlation and analysis
- Incident detection
- Security incident response
- Alert handling
- Crisis management
Rules relating to the protection of systems
- Identification
- Authentication
- Access rights
- Administrative accounts
- Management information system
- Compartmentalization
- Filtering
- Remote access
- Installation of services and equipment
Compliance with the LPM is achieved through certification. This means that an activity can only be operational if it has been validated by the certifying authority before it can begin.
NIS-2
History
In an increasingly interconnected European market undergoing rapid digital transformation, the reality of an unequal cyberwar between increasingly sophisticated and well-equipped malicious actors and economic entities that are too often unaware of cyber concerns The idea of acting collectively to ensure adequate security conditions throughout the Union is no longer a matter of choice, but a necessity. Inspired by the LPM, the NIS Directive, passed in 2016, followed by NIS-2, passed in 2022 and applied nationally in 2024, is entrusted with the pursuit of a highly strategic objective in this context: to certify a high and common level of security for all networks and information systems in key economic sectors of the European Union in order to raise the cyber maturity of Member States and better protect their economic and social interests.
The NIS-2Directive is therefore the European Union's response to the exponential growth in cyberattacks.
Scope
The transition from the NIS-1 Directive to NIS-2 marks a significant evolution in the European legislative framework for cybersecurity, particularly with regard to its scope.
NIS-1 mainly applied to operators of essential services (OES) and digital service providers (DSPs). OES included a range of sectors such as energy, transport, banking, financial market infrastructure, health, drinking water supply, and wastewater management. DSPs, meanwhile, included online marketplaces, online search engines, and cloud computing services.
NIS-2, which succeeds NIS-1, significantly broadens the scope of application to include new sectors such as postal and courier service providers, waste management companies, and certain public sector entities. It also includes the concepts ofSignificant Entities(SE) andEssential Entities (EE).
Am I affected?
To determine whether a company is affected by the NIS-2 Directive, it is essential to consider the following points:
Size of the entity: The NIS-2 Directive generally applies to medium-sized and large companies operating in the sectors covered by the Directive.
- A medium-sized enterprise is defined as a company with more than 50 employees and a turnover of morethan €10 million.
- A large company is defined as a company with more than 250 employees and a turnover of more than €50 million.
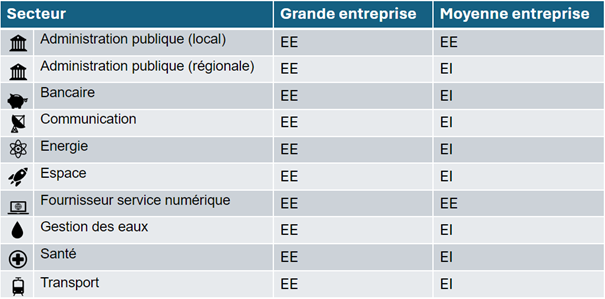
Sectors of activity: The directive covers nearly six hundred different types of entities, spread across eighteen distinct sectors of activity. These sectors are divided into two categories. Depending on their size, they can be considered as EI or EE.
Below is a non-exhaustive list of the companies concerned, according to their sector and size:
If your company recognizes itself in these elements, or if it is a service provider for another company that recognizes itself in these elements, you are most likely subject to NIS-2.
Obligations
The transition from the NIS-1 Directive to NIS-2 represents a major development in the European cybersecurity landscape. It still needs to be implemented at the member state level, but here is a summary of the obligations associated with each of these directives:
Obligations under NIS-1:
- Employee awareness
- Incident management
- Incident reporting
- Network monitoring
-Cyber resilience
Changes with NIS-2:
- Scope extension: NIS-2 broadens the scope to new sectors as specified above, with EIs and EEs replacing OSEs and FSNs.
- Enhanced obligations: Entities covered by NIS-2 must not only implement security measures but also manage risks related to the supply chain and product safety.
- Increased cooperation: It strengthens cooperation between Member States, in particular through the CyCLONe network ( Cyber Crisis Liaison Organization Network), which brings together ANSSI's counterparts at the European level.
Unlike the LPM, NIS-2 does not involve certification. This means that it is technically possible for an activity to be operational without complying with NIS-2. However, in the event of an inspection revealing a significant deviation, a heavy fine may be imposed, the amount of which is determined according to whether it is an EE or an EI.
NIST Cybersecurity Framework 2.0.
History
On February 12, 2013, the US government issued an executive order mandating NIST, the agency that provides standards for businesses, to develop a framework to strengthen the cybersecurity of critical infrastructure. Initially limited to government agencies and then to the US market, the NIST-CSF quickly expanded to include all activities seeking to improve their cybersecurity maturity. However, in ten years, the environment has changed and the acceleration of technological advances has been accompanied by a proliferation of cyber threats. An update to the CSF was therefore necessary. Published on February 26, 2024, NIST-CSF-2 extends its application to support all organizations, regardless of size and sector, in managing their cyber risks. This new version emphasizes the importance of governance and securing supply chains.
NIST-CSF 2.0 is therefore intended to be a global benchmark for cybersecurity risk management.
Scope
Apart from a few American institutions that have no bearing on Europe, there is no regulatory obligation to apply the NIST-CSF 2.0 measures. Implementation is left to the discretion of companies that have recognized the challenges of digital technology and wish to rely on an international benchmark to strengthen their security as much as possible.
Am I affected?
Therefore, although this falls outside the scope of the law, the question may arise as to whether or not it is appropriate to apply the measures. You may be advised to apply these measures if you are responsible for an economic, industrial, or governmental activity with a strong digital presence.
However, you do not need to apply NIST-CSF 2.0 if you are an individual or if you are already subject to a comprehensive cybersecurity framework specific to your sector (such as the LPM or NIS-2).
Obligations
NIST-CSF 2.0 is structured around six key functions:
- Govern : This function concerns the strategic management of cybersecurity. It involves establishing policies, processes, and responsibilities to guide security decisions. It is in this area that NIST-CSF 2.0 differs most significantly from its predecessor.
- Identify : Identification involves understanding assets, vulnerabilities, and threats. This helps determine security priorities.
- Protect : This function aims to implement protective measures to reduce risks. This includes physical security, access management, and user awareness.
- Detect : Detection involves monitoring suspicious activities and quickly identifying security incidents. This enables a more effective response.
- Respond : The response function involves immediate action in the event of a security incident. This includes incident management, communication, and recovery.
- Recovery : After an incident, recovery aims to restore services and learn from events to improve future resilience.
Each function is divided into categories, subcategories, and informative references, enabling organizations to create or improve their cybersecurity risk management programs.
It is important to note that CSF-2 is voluntary and does not prescribe how to achieve the desired results.
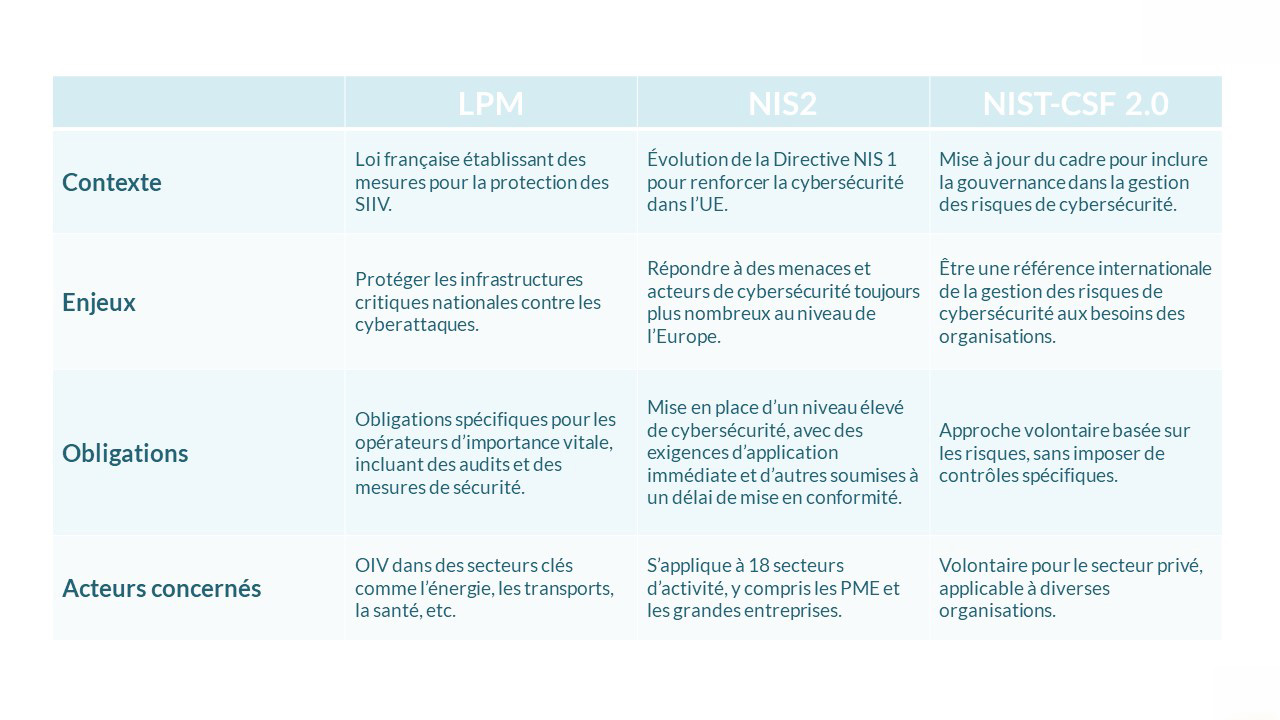
LPM, NIS2, and NIST 2 at a glance
Guillaume TURCAS
Cyber Risk Security Consultant