It is a fusion of CSPM (Cloud Security Posture Management, alerts on risky configurations), CWPP (Cloud Workload Protection Platform, alerts on containers and VMs), CIEM (Cloud Infrastructure Entitlement Management, mutualizes IAM), and much more (Infrastructure as Code scanning, secret discovery, etc.). There are about fifteen publishers that claim to provide this type of service.
Having participated in several RFIs/RFPs on the subject, here are some points to consider when making your choice.
Every hero has an origin story.
CNAPP is the buzzword in cloud security (for excellent reasons). Every provider will say they are a complete CNAPP, but in reality they will have expertise in a particular area (CSPM, CWPP, or CIEM depending on the functionality of the original product) and the others will be slightly less relevant. If you use a lot of containers/Kubernetes, choosing a CNAPP from a recognized CWPP will be a consistent strategy. On the other hand, if you use cloud resources extensively, a CSPM will be more appropriate.
Knowing your supplier's history is important!
The market is still young
The market is three years old with around fifteen players. Some are involved in legal disputes, such as Wiz and Orca for intellectual property theft, which is costing them market share despite their status as challengers/unicorns. There are few "pure players"; most are backed by a large company (Microsoft, Palo Alto). It is difficult to predict who will still be around in three years' time (e.g., Wiz's attempt to acquire Lacework).
Knowing who to build a relationship with is important for long-term cloud security (mergers/liquidations are expected within three years)!
Frankenstein effect
Several vendors started with one feature, but rather than developing the others themselves, they simply bought products that covered them. The result? An inefficient interface because there is no integration between products: in CI/CD scans, you can see the code and vulnerabilities, but you cannot identify the containers where it is deployed. You have to go to the container section to see which ones are affected. This will certainly improve, but integration is a slow process.
Having access to relevant information from anywhere is key, as is the supplier's integration capability.
Contextualizing risks
As soon as you connect your CNAPP to your cloud environments, it will raise thousands of alerts, which could overwhelm your DevOps and cybersecurity teams. Fortunately, the risk contextualization feature is there to sort and prioritize alerts according to their criticality.

While testing a solution, a high-level vulnerability was identified in my Azure subscription. Somewhat surprised, I decided to investigate. The problem was that there was an NSG (Network Security Group) that allowed port 22 from the internet, but it wasn't connected to any instance/subnet. There was no risk, and I wasted time on an irrelevant alert...
The relevance of alert prioritization must be confirmed during the POC before signing!
CSP coverage
It's pretty obvious, but the list of supported cloud providers can drastically narrow down your choices. Almost everyone supports AWS/Azure/GCP, but requirements for OCI, Alibaba, and IBM can make a difference and reduce your list of options.
Also, be mindful of what "cover" means: are all resources properly accounted for? Is IAM managed?
It is essential to verify that the capacities are equivalent between the CSPs you use.
Agentless
Most solutions are agentless, unless you need the CWPP part. To get the best view of Kubernetes, you will need to install the agent on the various nodes. This is relatively easy and the procedures are well guided. However, you need to consider the potential impact of this agent on performance. It can use between 300-700 MB of RAM and 3-7% of CPU. Some provide the ability to automatically shut down the agent during peak loads, although I don't recommend this from a security standpoint.
Checking agent consumption and its potential impact on your applications is key during the POC.
Integration
Each provider promises very fast integration with your cloud resources, which appear in less than two hours. This is true, but the most important part will be integration with your tools: SIEM for sending the most critical vulnerabilities, Jira or equivalent for creating tickets that developers must process, CMDB if you want your resources to be reported back to your traditional tools.
You must also verify that the registration is done at the tenant/organization level so that no subscription/account/project escapes monitoring.
The ability to write your own rules/controls is also key and may be necessary for demanding customers to see if it can be done easily (some are allergic to Regex).
Interface
UI/UX is obviously key. The initial approach is to think of it as a security tool that should be used by cyber teams. But it is much more effective if it is also used by DevOps teams with clear and pragmatic content.
Below is a CVE for which the vendor has not yet released a fix.
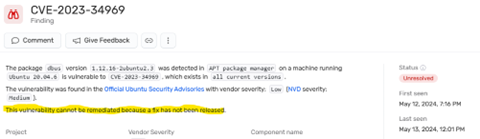
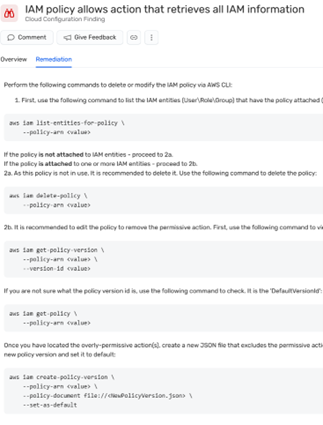
Here is a step-by-step explanation of how to fix it.
This will facilitate the adoption of the product by operational teams to prevent cyber teams from becoming a bottleneck.
The attack path diagram is also very effective for presenting a problem to management (for arbitration or to explain an incident).
Indirect competitor
Native CSP tools
The three hyperscalers offer their own tools, which is a good point of comparison during the POC. They are relevant and integrate very well with each other when using a single CSP. However, the fragmentation of information across multiple tools reduces efficiency when using multiple CSPs.
Open Source
Choosing an open-source solution is complicated because you have to keep up with updates to CSPs and threats. One customer equipped itself with an open-source CSPM, and despite having a dozen people dedicated to its maintenance, it was not possible to produce controls for multiple CSPs on the requested resources.
Note : a question to ask CNAPP publishers about the time it takes to cover new cloud resources with their controls (Azure Open AI is a good recent example).
Conclusion
I haven't written an article on why you should choose a CNAPP because every time I demonstrate it to CISOs and DevOps, I get a "wow" effect. The question is not "Will you need a CNAPP to improve your cloud security?" but rather, "Which CNAPP should you choose?"
It should be noted that, beyond the tool itself, establishing a clear and consistent vulnerability management process will be a key factor in the success of this type of project!
I hope this article will help you make an informed choice!
Matthew GAILLARD-MIDOL
CloudSec & SecOps Practice Leader







