Today, I'm going to give you an overview of the main features of Identity Governance and Administration ( IGA) solutions.
I have been a cybersecurity consultant for four years: I worked for two years in the field of IGA solution integration IGA solutions (specifically SailPoint's IdentityIQ solution) and have spent the last two years developing a reporting and dashboard solution for IAM tools.
An overview of the features of IGA solutions
Identity management
The IGAincludes the management of identities and their lifecycle within the customer's organization .
Identity management involves building a single centralized repository containing all identities and their information.
Identity lifecycle management involves detecting important events and triggering associated processes.
Finally,everythingthisismadepossiblebyfeaturesfeaturesbyplaybackandwritingonapplicationsapplicationsofIT.
The single, centralized repository
Managing IS users requires storing all IS identities and their information in a single repository.
The primary objective of thisreference system is to store and maintainimportant information relating to identity.
The applicationauthoritarian
Forthis,anauthoritativeauthoritativeisdefined.
An application is considered authoritative if it allows the creation of identities. Each account read on this application isanidentityof theIS.Thefirstreadingofthisapplicationcreatestheidentitiesofsystem.Bythe,ifa new account appears during reading, it will trigger the creation of a new identity.
Authoritative applications are generally human resources (HR) applications. There may be several authoritative applications: for example, if there is one HR application for external users and another for internal users. .
The IGA solution can be defined as the authoritative source. This involves initializing the solution by creating identities using another application defined as authoritative only at initialization. Subsequently, the solution is made authoritative by only allowing new identities to be created via the solution itself (by meansusingformsin).
Thecubeidentity
The authoritative application enables the creation of identities. Each identity is symbolized by its cube. The cube contains all known information about that identity. The first pieces of information are therefore those presentintheauthoritative application.
Byexample:wethereareoftenthename,thefirst name,theemail,thejob title, organizational unit, personal information such as work phone number and office, etc.
Added to this is all the information read from other applications, as well as accounts, permissions, and roles. and roles. Some information is not read but calculated from information that is read.
Ex: The manager can becalculatedbased onthe organizational unit, andtheactive/inactivestatusinthe company can becalculatedbased onthe start and enddates of the identity's contract.
Certain information can be configured to be editable in the solution interface. This allows information to be corrected or added. These actions can be configured to require approval andthesolutioncaninkeepatrace.
Once the identity cube is complete, this information can be written to non-authoritative applications. This enables automatic synchronization of identity information between the IGA solution and IS applications. applications.
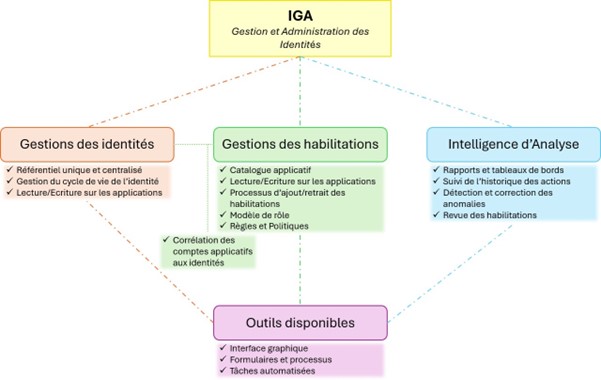
An identity cube from SailPoint's IdentityIQ tool is a good example: it contains identity information (not much in this example) and tabs are available to viewentitlements, applicationaccounts, events in the identity lifecycle identity (Events), etc.
AcubeidentityinIdentityIQresultingfromhttps://allidm.com/sailpoint-identityiq-create-identity/://allidm.com/sailpoint-identityiq-create-identity/
Identity Lifecycle Management
An IS identity goes through many stages throughout its existence in the IS. These stages are significant, and tracking them helps to limit anomalies such as authorizations that are not appropriate to the situation. ofororinformationinformation.
The implementation of processes associated with each stage enables automatic and seamless management of the identity lifecycle. identity.
Theeventstriggers
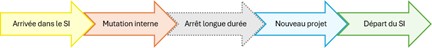
Example of an identity lifecycle
There are numerous events in the identity lifecycle. Each of these events requires the management of identity information and authorizations. Identity lifecycle events are specific to each information system, each environment, and each customer.
For each event, a list of factors is defined to determine whether an identity is experiencing the eventinquestion.
Ex:oneidentitycanliveitsarrivalintheSIwhenitiscreatedinthesolution:eitherviareadingreading the authoritative application, or via creation in the solution. But in another IS, an identity can be created when its contract start date arrives: it can therefore be created in the solution before its actual arrival .
Thefactors tobe listedbechanges in informationordates.
Ex: themanager changes,the organizational unit changes, so a change is detected; the contract end date triggers the departure of the identity; the end date of a project triggers the withdrawal of associated rights and roles. There may be several factors for the same event.
The precise definition of events and their triggers is an important step requiringthe client company to have a thorough understanding of existing processes and to give careful consideration to the matter: the side effects of a poor definition can be significant.
The associated processesassociatedto events
The detection of an event triggers an associated process. Processes are sequences of steps that enable bring identity into compliance with IT policies relating to the event in question.
Thedefinition of these processesis basedonthe company's IT policies andexistingprocesses. This is an area where change management may be necessary if existing processes are unsatisfactory in terms of security or efficiency,or ifthey do not exist.It is also an area whereadvice and best practices are crucial: creating or modifying processes can be a challenge for the client.
Thegeneric stepsof theseprocesses aremodificationandcalculation of information,removaland addingof rightsandandrolesroles,sendingofnotifications,thegenerationreportsreportsetc.
Example:for a transfer triggered by a change in an identity's organizational unit (OU), the steps may include calculating the new manager based on the new OU, removing the roles and rights associated with the old OU, adding the roles and rights associated with the new OU, notifying the managers and identities concerned, and generating a report containing the identities transferred on that day.
Processes are an important step in clarifying existing policies and implementing abettersecurityfor.
Provisioning provisioning
After triggering a process following the detection of an identity lifecycle event, it is time to update the IS applications with the new identity information and authorizations. time to update the IS applications with the new identity information and authorizations.
Thisstagepassesbythewritingwritingalsocalledprovisioning.
New identity information is written to its application accounts. New identity authorizations are updated in the applications: some are added and others are removed from the corresponding application accounts corresponding application accounts.
Finally,identityisonup to date,theapplicationsofITalsoandthe eventhasbeenhandled.
Here is an example of a functional view of identity creation management: it clearly shows the trigger process by recognizing the event " Creation of an identity", followed by the steps necessary to process the event in question.
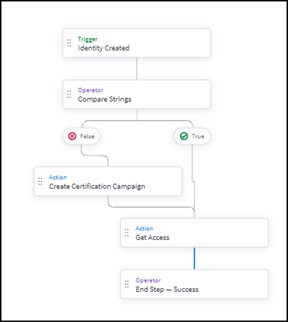
Aprocessofcreationofresultingfrom: https ://documentation.sailpoint.com/saas/help/workflows/workflow-basics.html
Authorization management
The IGAincludes the management of authorizations (or access rights) for identities within the IS.
Authorization management involves building a comprehensive application catalog, managing access requestsaccess requests, defining a role model, and creating a precise policy in terms of access rights.
The application catalog
Managing authorizations requires knowing all the authorizations on the IS and correlating them withcorrect identities.
This involves connecting the IGA solution to applications, reading application accounts, and establishing the correct correlatingbetweentheidentitiesof theSIandtheaccountsapplications.
Theapplicationapplicationismade upaccountsaccounts,groupsandauthorizationsreadontheapplicationsofIS.
Theconnectors
The role of the connector is to link the IS applications and the solution. There are multiple connectors, the main difference between them being the type of application to which they enable connection. For example, there are Active Directory, SAP, JDBC, CSV, XML connectors, etc. It is also possible to develop custom connectors to connect to types of applications not covered by the default connectors.
Each connector includes a configuration that allows it to connect to the relevant application. The connector allows data on the application to be read and written. Some applications are known as connectedordirect:it isthecasewhentheconnectorreadsandwritesdirectlytothe application.
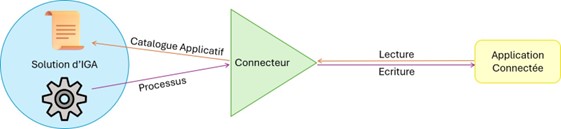
Theroleof theconnector-ConnectedConnected
Disconnected or indirect applications do not allow reading and writing from the solution:oneusuallyusuallyviafilesfiles(CSV)(CSVorXML).Itcreatedthefileflatbyextractingofdata from the relevant application. The connector allows the file to be read and objects to be created in the solution. When changes to the data in this application are necessary, the connector modifies the flat fileor creates a new one. The application updates itself by reading the most recent flat file available.
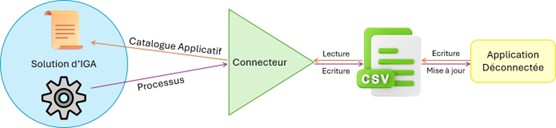
Theroleof theconnector-Applicationdisconnected
Reading applications
When reading applications, the solution obtains the objects present on the applications. The most common are application accounts, groups, and permissions. The solution stores all the necessary objects: this is the application catalog.
The correlation
Correlation rules enable each application account to be assigned to the relevant identity. To do this, information in the application account is compared with the same information in the identity cube.
Ifonesinglepiece of informationistomakethecorrelation,itistothe identifierofidentities:thismustbeone attributeuniqueandpersonal,differentforeachidentity.Ex:theemail,theusedorthetrigram.
It is also possible to use several pieces of information which, when combined, enable the application account to be assigned without riskerror.
Ex:thename,thefirst nameandthemaybe sufficientincertaincompanies.
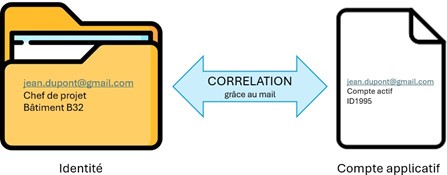
Correlationonthe addressemail
A study of data quality and the uniqueness of correlation factors is often necessary to verify certifythattherulesofcorrelationareadequate.
Accounts that cannot be correlated with existing identities from authoritative applications are the source the creation of new identities. However, non-correlatable accounts from other applications remain orphaned.
Theaccessfor access
Reading applications provides information on the status of the IS at any given moment. Authorization management is also handled also involves the automatic and seamless management of user requirements.
Requests to add or remove access can be triggered by predefined events. An event then triggers a process that includes adding and removing authorizations. Ex : Identity lifecycle eventsoften require the addition and removal of access rights. When an identity is transferred within the company,theaccesscorrespondingtoitsformerpositionareretiredandthosecorrespondingtoitsnewpositionareassigned.
It is also possible to set a specific duration for the granting of authorizations.
Example: At the start of a project, the necessary authorizations are assigned and the project end date is entered so that the authorizations are automatically withdrawn.
Finally, IS users can request the addition or removal of access rights themselves. Automated processes cover a large part of user needs and are designed to minimize additional requests. Special cases are handled via individual requests made by usersin thesolution. Adedicated process is defined to manage these requests. Ex: users have access to a form that allows them to request the addition or removal of access. When a request is made, the process ofgranting or revoking accessgenerally involvesapprovalsby the manager andadministrator of the application concerned . Once the process is successfully completed, permissions can be granted and applications are updated.
The definition of processes and forms related to access requests is highly customizable and must be carefully considered. Users can make these requests directly from the solution's interface, both for themselves and for the employees they manage. Access requests can be configured to automatically generate notifications when a request is created, approved, or denied. themselves and for the employees they manage. Access requests can be configured so that fieldssuch ascomments,datestartstartandendendof allocation,supporting documentationandotherarefilled outbytheby . Forms can also be configured to display important information to the applicant about accesses, such as description, roles to which they belong, associated risk, etc.
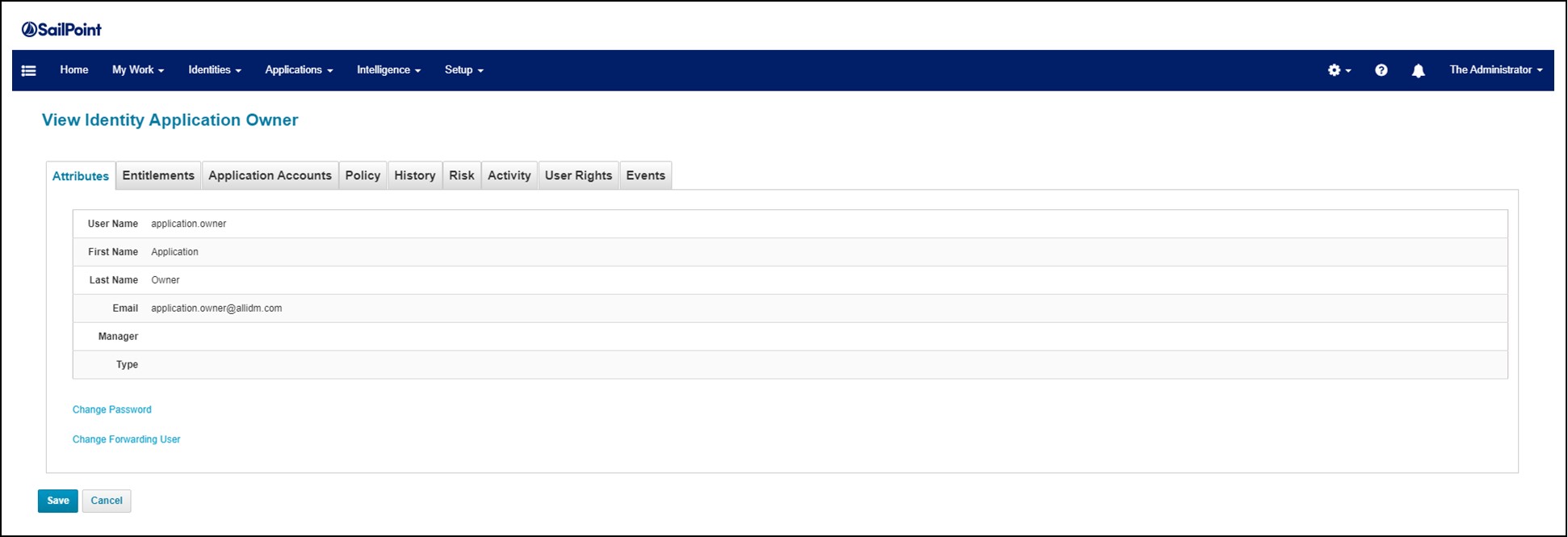
A simple access request form from SailPoint's IdentityIQ tool is a good example: it showsthefirsttabof anaccessaccessforyourself.Itareareatabtorequestaaddaccessandone otherforwithdrawalsaccessaccess.Theaccesstothe screenareauthorizationsauthorizationsandarole.Wecaninformationinformationthe concerning.The secondtab isareviewforrequest toverify that itis correctbeforesubmitting submit it.
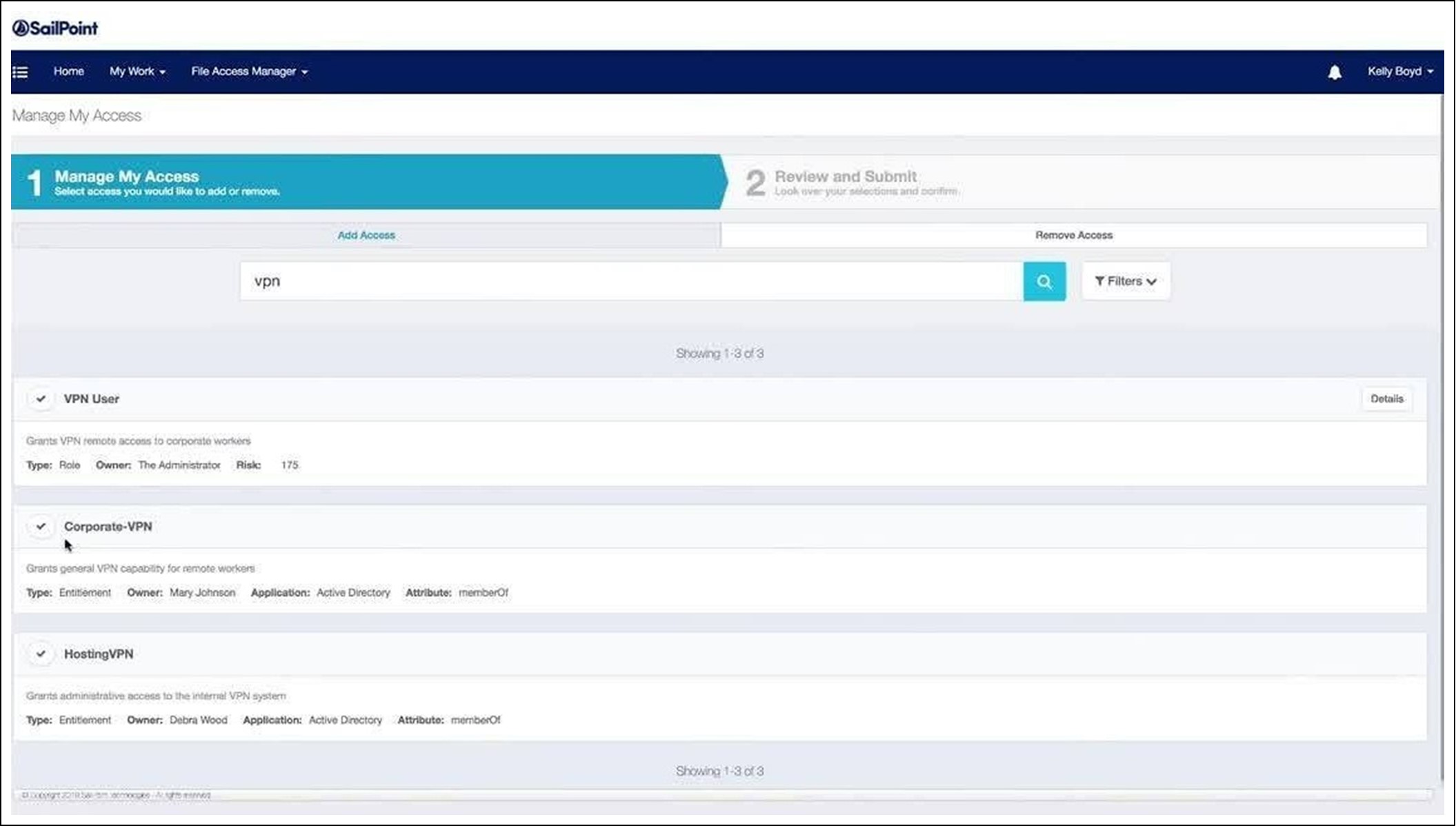
AformapplicationaccessaccessinIdentityIQ resultingfromIdentityIQAccessRequestsbySailPointTechnologiesonYouTube.
Themodelofroles
Roles are sets of characteristics that bring together identities and grant permissions.Defining roles simplifies the assignment of access rights and their subsequent review.
The role model can be defined by the employees themselves: each manager is asked to gather the necessary authorizations to work in their team. This creates a role model based on job functions and business units.
IGA solutions generally have a role extraction feature that allows you to define observable roles from the application catalog correlated with the identity repository. The solution itself identifies the commonalities between identities that have the same set of access rights.
The role model is an asset for an effective and secure IGA solution .
- Usersusersareassignassignedagamesetcoherentwithouthavingtodoarequest.
- Understanding access is simplified: the role has a clear name and description, unlike the multiple technical accesses it comprises.
- Access requests are easier to make and approve: a clear role rather than an undefined access list..
- The risk of requesting and obtaining unnecessary rights is reduced.
Thedifferenttypesofroles
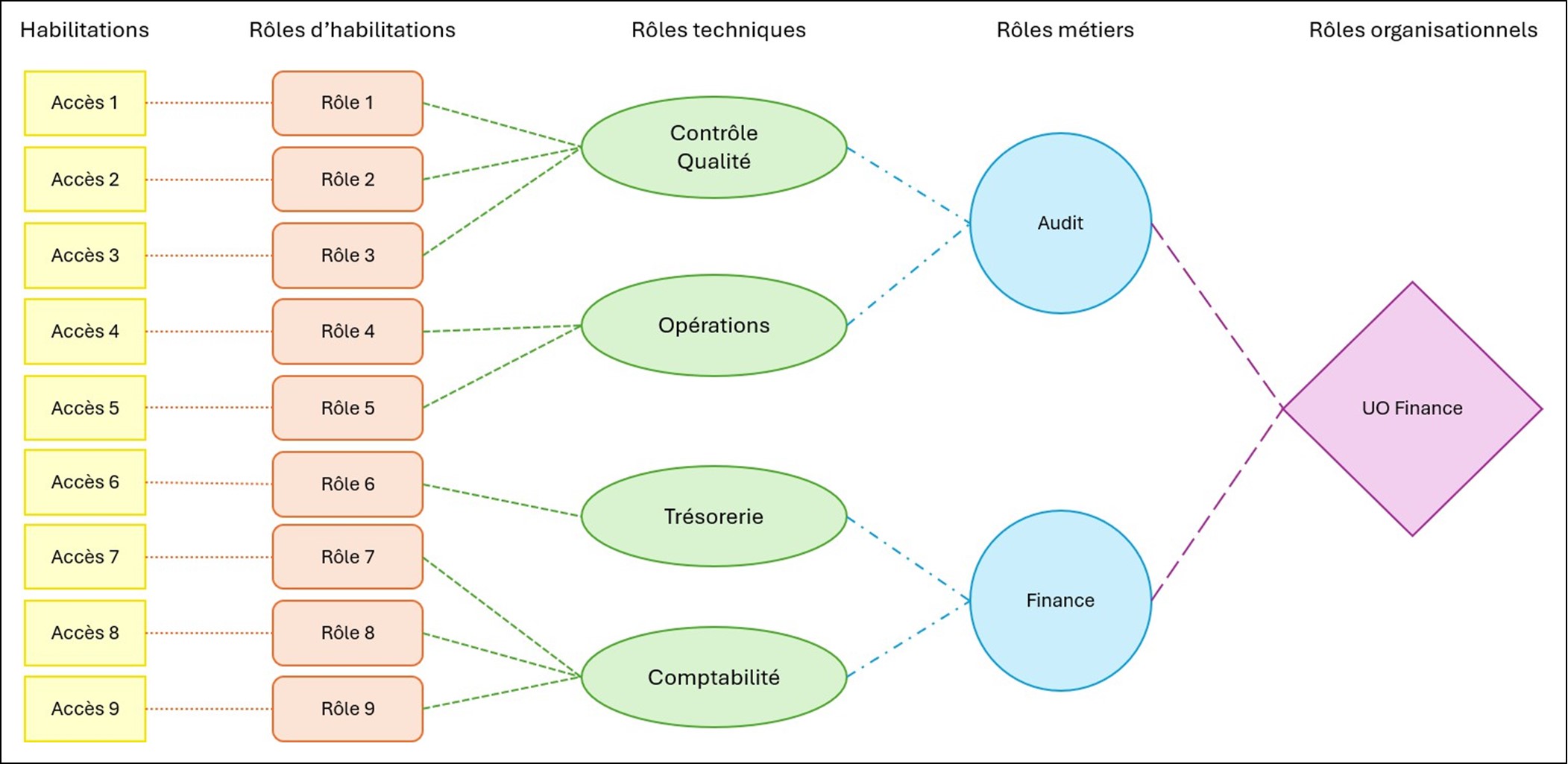
AnexampleofmodelofrolesfortheFinance
Amatrixofrolescompletehasseverallevels.
- Therolesof authorizations(inorange)combinearighttotoitsfunction
- Therolestechnical(ingreen)combineasetofrolesof authorizationstooneneedtechnical
- Business roles (in blue) associate a set of technical roles with a business function or task characteristiccharacteristic of a profession.
- Theroles((inpurple)combineawholeofrolesbusinesstooneOU
Rules and policies
Afeature ofIGA solutionsis theability todefinerules and policies to ensure the security of the IS.
Themechanismssuch asseparationseparationtaskstasks(Segregationof- ties - SoD) automatically verify the consistency of rights and access with the rules in force and to report anomalies. SoDis based on associations of rights,access,and accounts that are prohibited . The solution can prevent these associations from occurring by prohibiting an access request if it is not compatible with the access alreadypossessed.
Tasksautomaticautomatictocompletetheviolationsofitsrulesare put in place. If a rule is broken, notifications can be sent,auditsare triggeredto keepa recordof the eventand theprocessescanbelaunchedtocorrectthe anomaly.
Theguysofpolicyresultingfromhttps://community.sailpoint.com/t5/IdentityIQ-Wiki/Separation-https://community.sailpoint.com/t5/IdentityIQ-Wiki/Separation-of-duties-SoD-best-practices-in-IdentityIQ/ta-p/178004#toc-hId–192551779
Analytical intelligence
Thepartintelligenceanalysisis basedonseveralneeds:
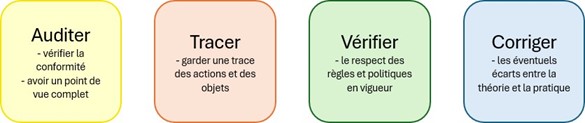
TheneedsforinIGA
Within a solution that centralizes all identities and applications, features such as audits, reports, and searches provide a clear view of the IT system and keep a history of actions and the status of the IT system.
Compliance with the policies in force in the IS is ensured by anomaly detection and correction features .
Usersuserscanalsoraiseandcorrectanyanomalieswhenreviewsreviewsaccessaccess points.
The analysisofdata
Tools such as reporting, dashboards, and search engines are available in IGA solutions to help administrators of these solutions manage the IS as effectively as possible.
Reports and research
Audit reports are simple, informative, and concise. They are triggered by a list of actions. ofthat have been defined in advancethatthecustomerwishestrack.Ex:the actionofrestartofthesolutioncanlaunchanaudit report that includes the time of the restart and the time required. Audit reports can also be configured.audittoeachcreationwithwiththe hour,thedate,theinformationofidentityinquestionandthesource.
Specific reports are more detailed, comprehensive, and complex. They are configured to meet the customer's information needs and to be exported. They can be created as needed or configured to be generatedon a regular basis.Ex:theaccountsonanapplicationwhosethelicensesarepaidcanbesubjectsubject to specific report, which could include columns such as the first and last names of the identities concerned, the date of creation and last use of each account, and the associated rights.
Reports offer a multitude of possibilities, and the most relevant ones will depend on the context and the customer's needs. of the client.
Advanced and customized searches allow you to search for objects in the solution and provide a greatamount of information.The searchesare easily configuredsimply fromthe graphical interfaceby the client and provide a quick overview of the identities, accesses, and authorizations present in the solution. Well-configured searches can result in the creation of a new report.
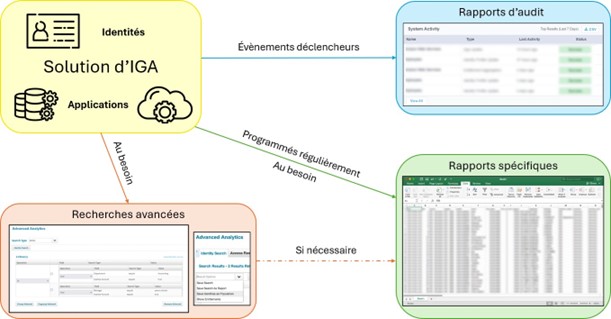
Theanalysis featuresanalysisofdata thatthreeimagesfromfromIdentityIQfromSailpoint
Detection and correction of anomalies
In the event of a proven discrepancy between theory and practice, the system must be able to identify anomalies, raise the alarm, and resolve the problem or enable users to resolve it quickly.
Detection
Alertsalerts maybe putset upwhenanomalies havebeen detectedby theIGA solution. If these alerts are intended for users, notifications are displayed or emails are sent. If the solution is designed to manage these anomalies, these alerts will trigger processes.
Both solutions can be used together: user notification and triggering of a dedicated process.dedicated process.
Reportsauditcancanbegeneratedbythesealertstokeeptracktrackofthe event.
Correction by solution
If the anomalies detected are predictable, processes are defined to remedy them automatically, quickly, and without intervention from IS users. The customer must define the key steps to address each alert. This allows the solution to manage its own compliance with the rules in place. In addition, anomalies that may represent security breaches for the IS are remedied without delay and the security of the IS is preserved.
Example:we are in an IS where it has been defined that passwords must be changed every 3 months. TheIGAlance solutionsendsan alert if a user's passwordis more than3monthsold.Theprocess can be to systematicallyrequest another authentication factor(answer to a question,code sent by email, etc.)whenthe user attempts to log in, then require a password change as soon as they are authenticated on the solution.This ensures thatthe solution's passwordpolicyis respected and the"Passwordtoo old "alert is handled directly by the solution itself.
User correction
Users of the solution can also resolve certain IT system anomalies. If human intervention is required to process an alert, forms can be displayed to the responsible users to obtain the necessary instructions or information.
When the anomaly is a unique case or no process can be generalized to resolve the issue problem, the responsible users will be notified and will correct the anomaly manually.
Ex:Theaccountsapplicationsapplicationsnon-authoritativethatarearenotcorrelatablewithidentitiesofSIareare. Theusersresponsibleofapplicationsconcernedcanthenreconciletheseaccountswiththeidentitiesthatown them.
If the specific case highlighted by the anomaly can be reproduced, a new rule will be defined. If human error is the source of this particular case, the anomaly will be processed and the alert will be archived.
Therecertifications
Recertification allows competent individuals to verify that the access, accounts, or roles granted are thecorrectandtorevokethoseinappropriatesuitable.
The setting
Acampaignforrecertificationisdefinedbyitsframework:whatisisbeing reviewed ?
It is possible to review the accounts, authorizations, and/or roles of identities. Recertification may apply one or more IS applications. The identities included in the recertification can be identified by acommon characteristic.Thepossibilitiesareendless.
For example:Re-certification of accesses classified as sensitive will be carried out for all identities with at least one sensitive access. All applications that offer so-called sensitive accesses will be affected.
Theapprovers
Arecertificationisalso definedalsobyitsapprovers:whoreviews ?
Frequent choices are identity managers and/or the managers of the applications concerned. It is possible to choose that recertification requires several approvals.possible to choose to have the recertification require multiple approvals.
For example:recertification may first require approval from the manager and then from the application manager. Approvals can also be delegated, meaning that the designated approver can choose to request another identity to approve the access in question. This is useful in the case of managers who are not familiar witha particular scopeand preferand prefer toask theproject managerapproveaccess.
Theconsequences
Finally,acampaignisdefinedbyitsconsequences:thatwhathappening ? Theaccess notreviewed aftertheendof therecertification maybe withdrawn,marked asdisapproved, or marked as unreviewed. Disapproved accesses can be removed as soon as the access is reviewed or at the end of the recertification process. They can be markedas disapprovedbut leftto the identitiespendingfor a managerwithdraws themhimself.
Criticalitycriticalityofobjectsreviewedduringofrecertificationrecertificationwilldefinedefinetheactionstotoin.
Thecustomizations
Email notifications are generally sent during recertifications. Approvers are notified at the start of the campaign and are regularly notified that they still have items to review until they have completed the process.
Detailed options such as comments, revocation dates, batch approvals, etc. allow define recertification campaigns that closely match customer needs. Policiespoliciescanbeputinbeforewhenrecertificationsrecertifications.
The principle of least privilege can be emphasized during recertification by clearly displaying which authorizations do not appear to be essential to the identity based on the individual's job, OU, and current projects. Approvers will then decide whether to retain these authorizations if they are necessary or to revoke them. The need-to-know principle can also be emphasized by reminding approvers that only authorizations that are truly useful to the identity should be retained. The fact of being able to have an authorization because one's job, OU, or current projectsis not sufficient grounds for granting authorization. Information meetings and notification emails can be used to remind approvers of these best practices .
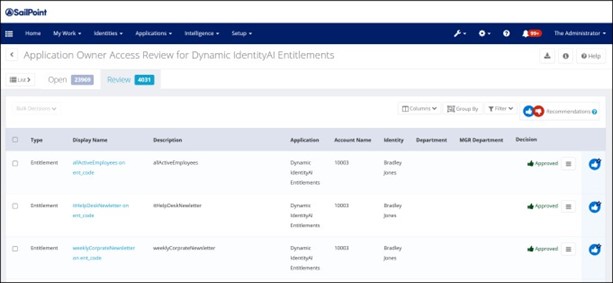
Exampleofaccessaccess
The tools available
Several highly useful features are available to enable IGA solutions to adapt to needsofcustomersandandintegrateintothelifeofcompany.
The graphical user interface
The graphical interface of IGA solutions can be customized to match the customer's brand: color codes, logos, and fonts are defined with the customer to closely match their usual graphic charter and ensure that the tool blends into the customer's environment.
The graphical interface can also be customized in terms of display, shortcuts, and features. Drop-down menus, shortcuts, and information displayed on the home page are to be defined with the customer. The home page must be intuitive, easy to use, and easy to understand for the solution to work well within the company. The most important features and information must be prominent and quick to access. Together with the client, and by observing the tools that are already in use, we define the best graphical interface for a project.
Finally, the graphical interfaceoffered to the usercan be customizedaccording to theirposition and OUorofhis/herplacein the hierarchywithinthe company.
For example:Employees will have a personalized interface allowing them to easily manage their own identity,accounts, and authorizations.Managers will havea different interfacetomanage both their own information and thatofthe employees they manage.Finally,OU managers will have an interface that makes it easier to view the different identities they manage, the tasks to be done (certifications, pending approvals, etc.), and the features they use most.
The interface can also be customized based on the options available to each employee in the solution.
Ex:alltheemployeeshaveaccesstothefeaturesfeaturesconcerningastheapplicationfor authorizationandthevisibilityofinformationrelatedtotheiridentity.Moreprivilegesprivilegesinthe companyareimportant,thethefeatures ofthesolutionareavailable:webelieveintoanalyticalanalyticalthatto obtainreportsreportsanddashboards dashboards on the identities and applications of the IS that are only available to certain employees.
The level of customization of the graphical interface and home page requires careful consideration of the company's organizational structure and the needs of each employee. The more accessible the interface, the more solutionwill integrateintothelifeofcompanyandwillanasset.
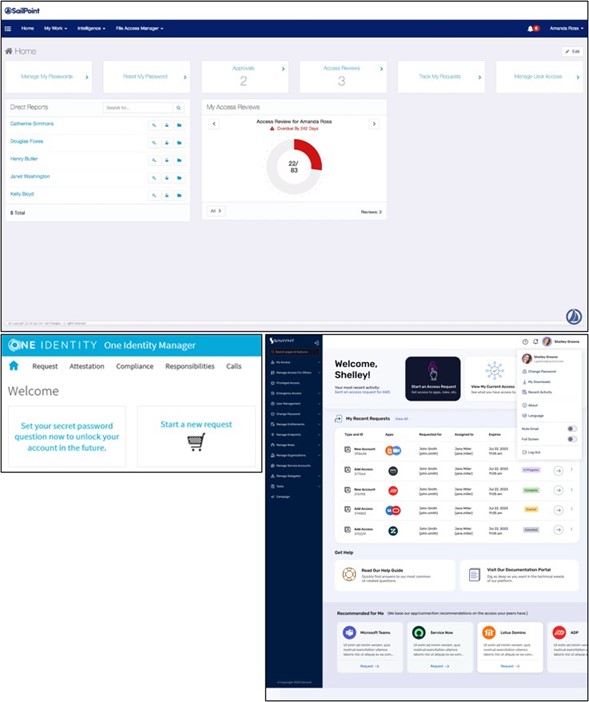
ExamplesexamplesofhomehomesolutionssolutionsIGA
Theforms
IGA solutions have forms to request certain necessary information from users .foroperationofthesolution.
Forms can be used for features such as access requests, identity creation, and changes to identity information (moving, transfer, etc.). In this case, filling out the form is the first step in the process, and the form is permanently available to users.
Forms can also be steps in processes. In this case, the form only appears when the information is needed for the process, in the form of a pop-up, and will no longer be available once validated.
The fields in a form are customizable: clickable lists, formatted fields (Last Name First Name), dates,calculated fieldscalculated andnon-editable(calculated managerbased onof thechosen),default valuesdefault that can be modified, etc.
Thevalidationof aformlaunchesaprocesstailoredandtakingintoaccounttheinformationentered.
One of the challenges is to make them very easy to use by adapting them to the target users. Tests of the forms under development can be carried out on a panel of future users to take into account as early as possiblethe designany comments from. Adaptasclose to theforms andprocesses already existingallowstotolimitthedrivingofchange.
Automationof tasks
Tasks enable the solution to be updated automatically. They can be launched manually as needed, scheduled to run regularly, or scheduled to run at key times (a tasktaskterminatingwitharesultpreciseintriggeraanotherbyexample).
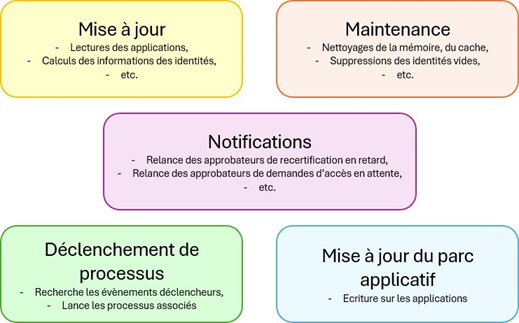
Exampleofdifferent tasks
Task sequences can be scheduled for solution updates or other regular requirements andtoosignificanttobemanagedbyonesimpleprocess.
Ex:Updating the solution may require :
- Readthedatafromthe authoritarian application
- Update identity cubes
- Triggertheprocessesofcreationprocessessonewnewaccountshave appearedontheauthoritative
- Deletetheidentitiesthathaveanyaccountsaccountsontheauthoritarian,
- Readthedataofotherapplications
- Launchtheprocessesrelatedtopoliciesforverifycompliancecomplianceofauthorizationsandaccountsaccountsexisting
- Puttoupdatetheaccessfor(closethoseforforthereadingshaveshownthattheaccessareproperly assigned)
The available tasks and their results history enable maintenance of the solution without human intervention and important information traceability: thanks to the history, we know when the informationwasobtainedandprocessesprocessesareinitiated.
Mariann FAURE
Cybersecurity Consultant





