
EveryOps Matters: Towards Dev, Sec, Ops, and ML Convergence
AtDevSecOps Days JFrog Paris 2024, it became clear that the scope of modern software development goes far beyond simply writing code:
"The role of the modern developer is no longer limited to producing code. They must master management, security, integration, orchestration, and supervision, while collaborating closely with Data Science and Machine Learning teams." (Eyal Rudnik, JFrog Paris 2024)
This transformation is taking place in a context where the complexity of infrastructures and the interconnection of systems require an integrated approach. Silos between development, security, and operations teams must be reduced to ensure smooth and effective collaboration. Such convergence improves developer productivity and system resilience in the face of emerging threats.
📉The economic and strategic impact of AI in DevSecOps
Artificial intelligence is emerging as akey factor in reducing costs and optimizing performancein DevSecOps cycles.
According toMorgan Stanley, 94% of companies anticipate using AI in production by 2026. Gartnerestimates that 80% of organizations will adopt integrated DevSecOps platforms by 2027. This transition is driven by increased automation of repetitive tasks, reduced vulnerability-related costs, and improved scalability of production environments.

The economic impact of this transformation is significant. Companies that integrate AI into their DevSecOps pipelines are seeing reduced application deployment times and improved anomaly detection. Thanks to machine learning models, it is now possible to anticipate failures and automate corrections before an incident occurs.
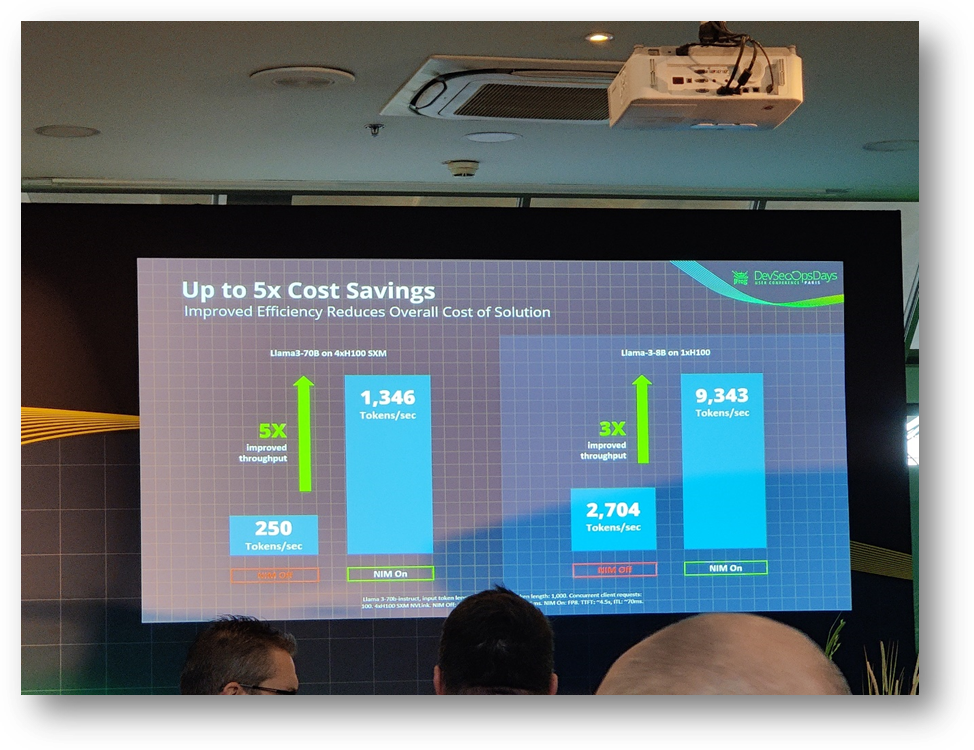
💡 Use case: The integration ofNVIDIA NIMwith JFrog has demonstrated a3x to 5x improvement in AI model throughput, significantly reducing inference costs and optimizing operational performance.

🔐Complete security: from correction to active monitoring
JFrog's State of DevSecOps 2024reveals that only56% of organizations perform combined scans of their sources and binaries. This gap creates a significant blind spot in vulnerability management, increasing the risk of compromise in production.
With this in mind, JFrog has introducedRuntime Security,an advanced solution that facilitates instant detection of vulnerabilities in operational environments, correlates production binaries with their source code, and optimizes the time required to fix critical security flaws.

One of the major challenges lies in implementing continuous monitoring mechanisms that enable rapid identification of emerging threats and improve mean time to remediation (MTTR). By adopting tools such as Runtime Security, organizations can automate and contextualize their remediation cycles, ensuring a rapid and effective response while minimizing operational disruptions.
📍 Case study: APyPi token exposed for 18 monthswas detected and revoked inless than 17 minutesafter disclosure (JFrog Research, 2024). This incident demonstrates the need forcentralized and automated management of CI/CD secrets, thereby reducing the risk of malicious exploitation and improving the overall security posture of systems.
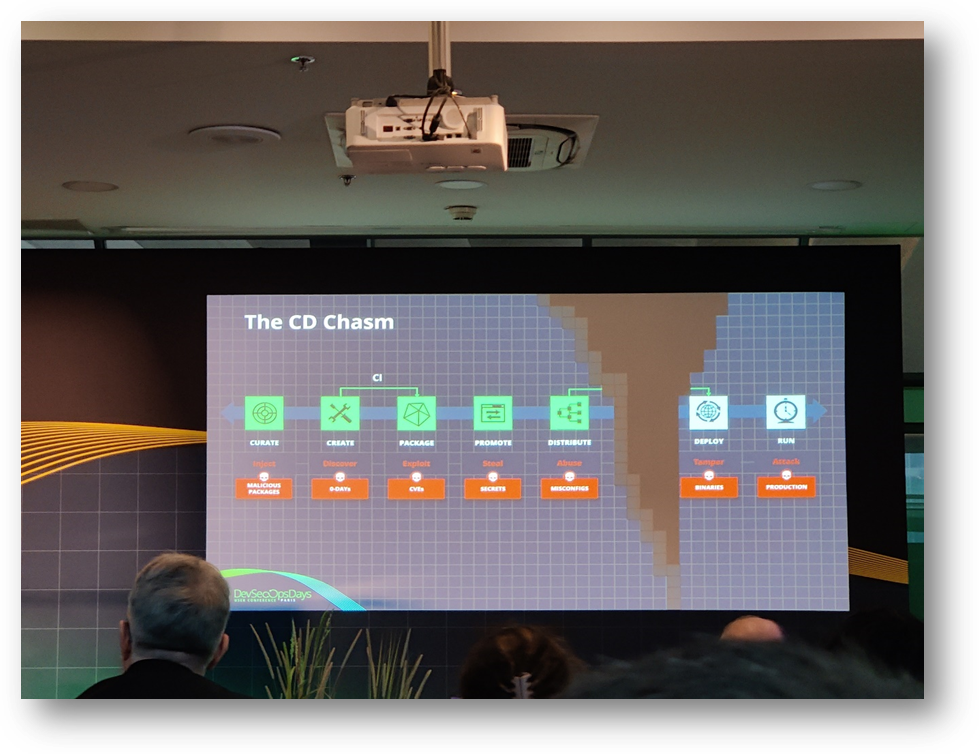
🏗Bridging the "CD Chasm": Towards Intelligent DevSecOps Orchestration
TheCD Chasm(Continuous Delivery Chasm) illustrates the security gaps between development and production. Major risks identified include accidental injection of secrets into compiled binaries, unmonitored vulnerable open-source dependencies, and vulnerabilities that can be exploited once in production.
Automating compliance checks and integrating security testing into every phase of the CI/CD cycle are essential to reducing these risks. Companies must also adopt a "Shift Left Security" approach, where security is integrated from the earliest stages of development rather than at the end of the chain.
📌 JFrog EveryOps solution:
- Proactive detection of secrets and vulnerabilities
- Continuous runtime monitoring
- Enhanced governance of dependencies and artifacts
📦MLOps: governance and security of AI models
According toGartner, 85% of AI/ML projects fail before reaching production. The lack of a standardized supply chain and the lack of governance over models are limiting factors.
The industrialization of AI models requires the integration of DevSecOps principles into MLOps workflows. It is essential to monitor not only the quality of the model, but also the origin and integrity of the data used to train it. This involves adopting secure model registries and rigorous version management.

JFrog offers an integrated solution that provides secure, single-source storage for ML artifacts, traceability for models and datasets, and adaptive deployment via strategies such asreplace, shadow, and custom.
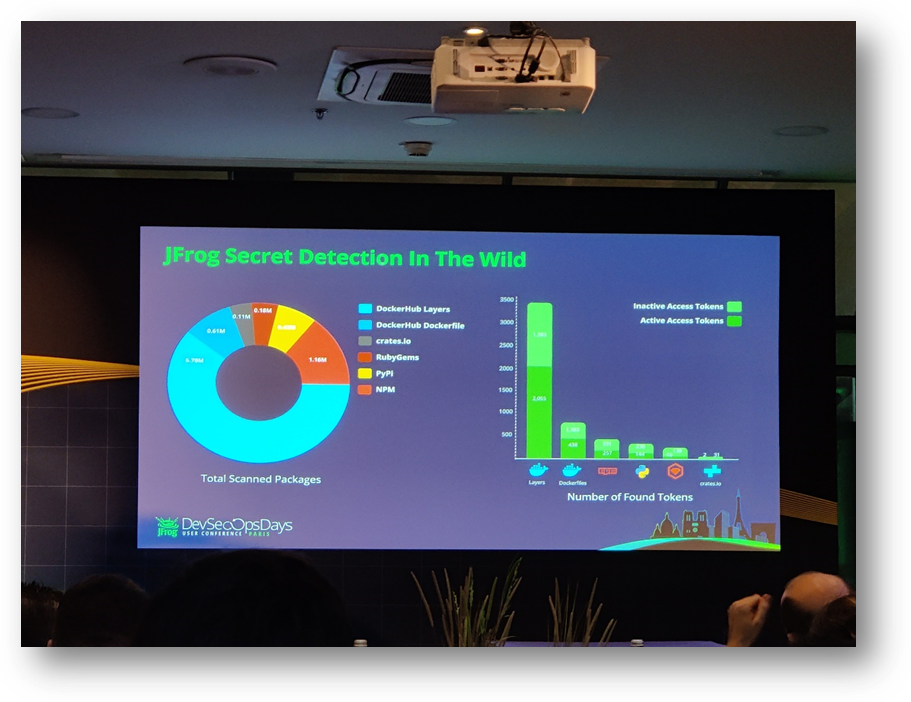
🛑Supply Chain Attacks: DockerHub and PyPi under increased surveillance
⚠20% of DockerHub repositories are considered malicious(JFrog X-Ray Report, 2024).
Attacks on the software supply chain have become a major threat to organizations. The example of infected packages on DockerHub and PyPi shows how carefully trust in open-source ecosystems must be managed.
📌 Recommended measures:
- Locking dependency versions
- Restrictions on the use of unverified packages
- Continuous vulnerability scans and enhanced remediation policies
🔥GitHub x JFrog: CI/CD automation and security

The integration between GitHub and JFrog marks a significant step forward with innovations such asGitHub Push Protection, which automatically blocks exposed secrets, and advanced integration of security scans into GitHub Actions.
Tools for protecting secrets and analyzing CI/CD pipelines must become industry standards in order to reduce the risk of accidental leaks and compromise critical infrastructure.
🎯Conclusion: towards comprehensive DevSecOps security
DevSecOps Days JFrog Paris 2024highlighted the key trends:
- End-to-end security from development to production
- Integrating MLOps as native elements of DevSecOps
- Continuous monitoring and governance of the software chain

The presentations highlighted current cybersecurity challenges and innovative solutions for securing the software supply chain.
"Unsecure DevOps is not an innovation, but a potential vulnerability." (Gily Netzer, JFrog Paris 2024)
With anEveryOps approach,JFrog and its partnersdefine a robust framework that guaranteesscalability, efficiency, and securityin a cloud-native and AI-driven environment.


