Security experts are rare and overwhelmed. Developers want to do the right thing (they're not against it), but they don't have the time, the tools, or the visibility to know what's expected of them. As a result, security often remains a "best effort" issue until a breach (or audit) reminds us of its importance.
So how do we move from wishful thinking to real team dynamics? Spoiler: we avoid grand gestures and rely on two concrete levers. A framework (OWASP SAMM) and relays (Security Champions).
Getting organized without stifling your teams: how OWASP SAMM helps you move forward at the right pace
It is tempting to want to "ensure security" by piling up actions as they come up: a SAST scan here, a threat modeling workshop there, a one-off audit for reassurance. But without real coordination, it tires everyone out and disperses efforts.
OWASP SAMM (Software Assurance Maturity Model) is not a magic bullet. It is a compass. It allows you to know where you are (without lying to yourself), to define where you want to go, and above all to chart a progressive and realistic path.
The advantage? SAMM is based on your value streams. Your products, projects, and teams dictate the priorities. Not some abstract checklist. You structure your practices in a way that works for you, with a clear vision of the benefits. But for this approach to be more than just theory, you need people on the ground. People who know how things work in the heat of the moment. In short: craftsmen.
Security Champions, artisans of everyday security
A Security Champion is not a superhero or a security guru. They are a member of the team (often a developer or tech lead) who agrees to take on the role of "security" on a daily basis, without losing sight of delivery issues.
His role? To translate safety requirements into the language of the team. To suggest appropriate practices. To support his colleagues without holding them back.
(He is not there to police, but to facilitate. An essential distinction.)
For example, they can organize a security-focused code review on a sensitive topic, initiate a quick and easy threat modeling workshop, or help integrate a security linting tool into existing pipelines (without turning it into a year-long project).
It is these small touches, added with finesse, that bring about lasting change in practices. And for this to work, there must be a framework to build on. This is where SAMM becomes your best ally.
Supporting the SAMM & Champions duo: feedback from a field that is not always easy
In an organization I recently worked with, the situation was clear: several autonomous squads, inconsistent security practices, and a central security team unable to handle all the requests. Nothing new, but still a major obstacle.
The first step was to simplify the SAMM approach. No heavy auditing, but a quick mapping of existing practices. The goal: to identify critical value streams and focus on them.
Next, we identified Security Champions in each relevant team. Not necessarily the most security-savvy individuals, but people who were motivated, respected by their peers, and willing to take on this role.
The work with them was done collaboratively. Together, we defined simple actions to integrate into daily life: adding a check in sensitive PRs, equipping certain repetitive controls, and leading practical workshops.
Each step forward was visible: the Champions maintained a dashboard that tracked SAMM progress, but with meaningful indicators for the teams. No vanity metrics, just concrete facts: what we improved, what we stabilized, what we plan to do.
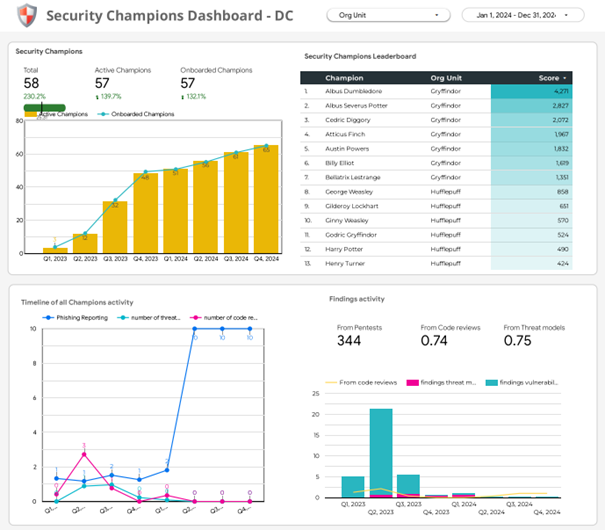
OWASP does a great job promoting security champions through a dedicated project that I strongly encourage you to check out. Here are some examples of dashboards to set up.
What really made the difference? Active sponsorship (on the tech and product side), regular engagement with the Champions community (discussions, sharing of practices, skills development), and above all, constant synchronization with the SAMM roadmap (no disconnect between the overall vision and the reality on the ground).
Common mistakes (and how to avoid them so that it really works)
Inevitably, there are pitfalls with this kind of approach. The most common one is appointing champions "on principle" without giving them the means to act. That's the best way to burn them out in three months.
Another common mistake is defining SAMM KPIs that do not resonate with teams' daily work. If your indicators do not speak to them, buy-in will be close to zero (and it will be your fault, not theirs).5620
And then there is the trap of isolation. A Champion left alone in their corner, without recognition or interaction, will eventually lose interest. Hence the importance of fostering a genuine collective dynamic, valuing their actions, and integrating them into product decisions.
Finally, trying to impose SAMM requirements without taking local realities into account is a surefire way to hit a brick wall. Alignment between the SAMM roadmap and each squad's priorities is non-negotiable (otherwise, it remains just one security project among many).
Security is primarily a matter for well-equipped teams, not isolated experts.
There is a lot of talk about security "by design." But it cannot be decreed. It must be built, step by step, with the support of the teams themselves.
With SAMM setting the course and Security Champions bringing best practices to life on a daily basis, you have a winning combination. It's not a magic solution, but it's a method that works because it respects the reality on the ground.
That's what true application security industrialization is all about: continuous progress, embodied by teams, structured yet flexible.
So, the question is simple: do your Security Champions have the space to act? Or are you still hoping that a central team will be enough to solve everything?
(If you are in the second situation, it may be time to reconsider your strategy.)





